Data protection and security protocols have become more robust in the last two decades. This has been driven both by increasing incidents of data breaches – statutorily acts such as the EU General Data Protection Regulation (GDPR), the Gramm-Leach- Bliley Act, Health Information Technology for Economic and Clinical Health (HITEVH) Act, Health Insurance Portability and Accountability Act (HIPAA), and the Fair and Accurate Credit Transactions Act – and by the Payment Card Industry Security Standard, to name just a few drivers. In general, most entities have implemented strong safeguards to ensure that issues such as inadvertently sharing identifying information with third parties and the existence of sensitive data (credit/procurement card numbers, tax IDs, social security numbers, vendor/customer bank account numbers, etc.) for their current and active data are addressed.
Though these measures have become more commonplace, the threat of cybercrime and data breaches is unfortunately still on the rise. Cybesecurity Ventures, a cybercrime magazine, estimates that cybercrime will cost approximately $10.5 trillion per year on average by 2025, up from $6 trillion in 2021. IBM estimates the average cost of a data breach for a company is $4.24 million per incident. This figure covers detection, containment, revenue loss and equipment damage, but there are also unspecified irreversible losses to the company’s reputation and goodwill. Even more worrisome during merger, acquisition, or divestiture activity is loss of intellectual property, the impact of operational disruption, and the costs of regulatory compliance. The below figure from Deloitte illustrates typical points in the M&A lifecycle that are dependent on data transfer, putting the involved companies at increased risk of cybersecurity threats:
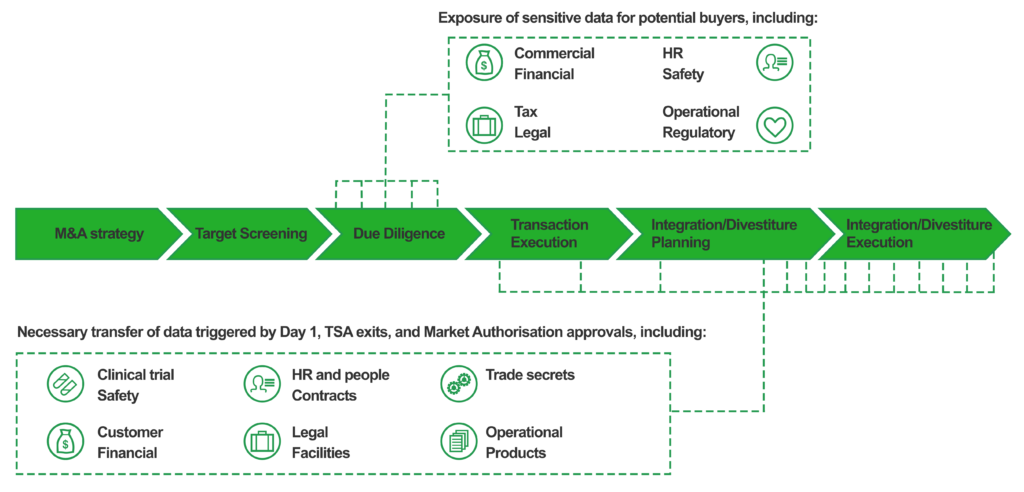
These threats are more likely to arise when a company has legacy or inactive ERP data. Prior to the enhanced security protocols of the last two decades, it was common practice to put sensitive data into an ERP system’s unsecured fields, such as memo and descriptive fields, or in otherwise re-purposed fields. As a result, much legacy data does not meet privacy and security standards. This risk can be managed without having the expense of a hygienic data purge when the legacy data is buttressed by access controls. The biggest risk is when a third party is given access to or possession of either a portion or clone of an existing ERP instance. This most commonly occurs in divestiture or partial divestiture situations.
In fact, it’s been speculated that undergoing complicated large-scale business changes (like a divestiture, an acquisition or a merger) opens an enterprise up as an easier target for a security breach because of infrastructure changes and limited resource allocation. This is an especially vulnerable time because if a parent company creating a clone for their acquired company still retains the data of a (now sold) child company and suffers a theft or data breach, not only do they have the downfall of their own reputation, but they could be liable for damages to the child for the compromise (or vice versa), compounding the threat if that company in question is flipped again and purchased by another entity. If they have data belonging to the parent company, they are at risk if any of the companies has a breach that involves the parent company’s data. As companies are repeatedly bought and sold, a data breach can be very costly for both the acquirer (parent) and the acquired (child) company. Over time, the original source of the data is not clear, and the breach can have untold impacts and ever-increasing costs. The bottom line is that all parties will bear the burden, monetary expense of remediation, and opportunity cost of a damaged reputation.
There has been an uptick in the handling of divestiture and acquisitions by cloning the instance in question, masking the data and handing it off as part of the sale – but there are inherent risks for both the buyer and the seller when using a clone or masking solution for a divestiture. Companies who are creating a clone for their acquired company still have data belonging to the child company, and therefore, they would not only have the reputation of their own customers, but they will likely have to pay the child company compensation for breach of their data. The reality is that an experienced hacker can undertake an unmasking initiative, access that data by finding related data, or querying at the data base level, and open vulnerabilities for both an internal and external data breach.
With the exceptional dangers involved, it begs the question: why have these processes become commonplace? The seller risks inadvertently sharing trade-secrets or competitive advantage via sensitive information left in the database, and the buyer undertakes the complication of carrying the masked data that it does not own in their system, causing delays and increasing infrastructure costs (i.e. a larger footprint, additional license fees, added expense to manually segregate the data for reporting or compliance, etc.).
This risk cannot be understated. A single inadvertent unauthorized disclosure of private customer or vendor information could result in large penalties, sometimes into the millions of dollars. If the clone instance is provided to a competitor in a partial divestiture, added to this risk is the possibility of damage resulting from inadvertent disclosure of the non-divested business’ proprietary strategic information, such as vendor and customer credit lines, discounts, customer and vendor contractual details, etc.
Finally, to magnify these risks, the threat of litigation losses respective of inappropriate data disclosure can dwarf the costs of other risks.
So what is an appropriate risk management strategy to adopt during a divestiture? An entity has three choices: minimize the risk, accept the risk, or ignore the risk.
Minimizing the Risk:
This strategy involves a variety of steps, including non-disclosure agreements with third-parties, contractual obligation, and other due diligence around the risks. However, the ideal way to minimize the risk is to purge old/legacy non-divestiture related data from the clone instance provided to the divested or acquired entity.
Accepting the Risk:
Accepting the risk can be an effective risk mitigation strategy. However, to accept the risk, entity management must have a relatively accurate estimate of the risky data exposure accompanied by a what- could-go-wrong quantification of the potential risk respective losses.
Barring a means to quantify the risks associated with the divested clone instance’s legacy and non- divested entity related data, entity management is not accepting the risk. Instead, by default, entity management has chosen the riskiest approach – Ignoring the Risk.
Ignoring the Risk:
If an entity’s management cannot be provided with a reasonable estimate of quantified risks associated with the divested clone instance’s legacy and non-divested entity related data, then barring minimizing the risk by purging unrelated and legacy ERP information, management has chosen to ignore the risks. This is the worst possible strategy, because it leaves the entity open to the risk of being deemed negligent, which can significantly exacerbate litigation, business and other risks
In conclusion, during the rapid transition of a divestiture, it is critical to ensure that due attention is given to the risk of legacy, inactive, and unrelated to the divestiture ERP data. The best strategies are to either minimize or accept the risk and avoid the unacceptable act of ignoring the risk.







1,300 thoughts on “Your Competitor’s Spyglass: Data Risks During a Divestiture”
casino olympe: olympe casino – casino olympe
kamagra en ligne [url=https://kamagraprix.shop/#]Kamagra pharmacie en ligne[/url] kamagra gel
cialis sans ordonnance: Tadalafil 20 mg prix sans ordonnance – cialis generique tadalmed.shop
cialis generique: Acheter Cialis 20 mg pas cher – Tadalafil 20 mg prix en pharmacie tadalmed.shop
Acheter Kamagra site fiable: kamagra livraison 24h – kamagra en ligne
http://pharmafst.com/# trouver un mГ©dicament en pharmacie
Cialis sans ordonnance pas cher: cialis prix – Achat Cialis en ligne fiable tadalmed.shop
cialis sans ordonnance: Pharmacie en ligne Cialis sans ordonnance – Tadalafil achat en ligne tadalmed.shop
http://pharmafst.com/# pharmacie en ligne livraison europe
pharmacie en ligne avec ordonnance: pharmacie en ligne pas cher – Pharmacie en ligne livraison Europe pharmafst.com
cialis sans ordonnance: Pharmacie en ligne Cialis sans ordonnance – Cialis en ligne tadalmed.shop
Acheter Viagra Cialis sans ordonnance: Acheter Viagra Cialis sans ordonnance – Cialis generique prix tadalmed.shop
Pharmacie sans ordonnance [url=https://pharmafst.com/#]pharmacie en ligne fiable[/url] п»їpharmacie en ligne france pharmafst.shop
kamagra pas cher: kamagra gel – Kamagra Commander maintenant
https://pharmafst.com/# pharmacie en ligne fiable
pharmacie en ligne sans ordonnance: pharmacie en ligne pas cher – pharmacie en ligne livraison europe pharmafst.com
Acheter Cialis 20 mg pas cher: Cialis sans ordonnance 24h – Acheter Cialis tadalmed.shop
https://tadalmed.com/# Pharmacie en ligne Cialis sans ordonnance
kamagra livraison 24h: achat kamagra – Acheter Kamagra site fiable
cialis sans ordonnance [url=https://tadalmed.shop/#]Cialis sans ordonnance 24h[/url] Acheter Cialis tadalmed.com
pharmacie en ligne france livraison belgique: Medicaments en ligne livres en 24h – pharmacie en ligne pas cher pharmafst.com
pharmacie en ligne livraison europe: Pharmacie sans ordonnance – pharmacie en ligne sans ordonnance pharmafst.com
https://kamagraprix.com/# kamagra oral jelly
Acheter Cialis 20 mg pas cher: cialis sans ordonnance – Cialis generique prix tadalmed.shop
kamagra 100mg prix [url=https://kamagraprix.shop/#]kamagra oral jelly[/url] kamagra gel
Achetez vos kamagra medicaments: acheter kamagra site fiable – kamagra livraison 24h
vente de mГ©dicament en ligne: Pharmacie en ligne livraison Europe – trouver un mГ©dicament en pharmacie pharmafst.com
https://pharmafst.shop/# pharmacie en ligne france pas cher
kamagra gel: Acheter Kamagra site fiable – kamagra pas cher
Pharmacie en ligne livraison Europe: vente de mГ©dicament en ligne – pharmacie en ligne pharmafst.com
Achat Cialis en ligne fiable [url=http://tadalmed.com/#]Tadalafil sans ordonnance en ligne[/url] Acheter Cialis 20 mg pas cher tadalmed.com
pharmacie en ligne sans ordonnance: Meilleure pharmacie en ligne – pharmacie en ligne france fiable pharmafst.com
https://tadalmed.com/# Pharmacie en ligne Cialis sans ordonnance
kamagra pas cher: kamagra pas cher – Acheter Kamagra site fiable
acheter mГ©dicament en ligne sans ordonnance: Medicaments en ligne livres en 24h – п»їpharmacie en ligne france pharmafst.com
Kamagra Commander maintenant [url=http://kamagraprix.com/#]kamagra pas cher[/url] kamagra oral jelly
https://pharmafst.shop/# Achat mГ©dicament en ligne fiable
acheter mГ©dicament en ligne sans ordonnance: Pharmacie en ligne France – pharmacie en ligne pharmafst.com
Cialis sans ordonnance 24h: Cialis sans ordonnance pas cher – Achat Cialis en ligne fiable tadalmed.shop
pharmacie en ligne sans ordonnance: Medicaments en ligne livres en 24h – pharmacie en ligne sans ordonnance pharmafst.com
kamagra en ligne [url=http://kamagraprix.com/#]achat kamagra[/url] kamagra oral jelly
https://pharmafst.com/# п»їpharmacie en ligne france
pharmacie en ligne france fiable: Livraison rapide – pharmacie en ligne sans ordonnance pharmafst.com
http://pharmafst.com/# trouver un mГ©dicament en pharmacie
pharmacies en ligne certifiГ©es: pharmacie en ligne – Pharmacie en ligne livraison Europe pharmafst.com
https://kamagraprix.com/# Kamagra Commander maintenant
achat kamagra: Kamagra Commander maintenant – acheter kamagra site fiable
https://kamagraprix.shop/# Achetez vos kamagra medicaments
Kamagra Commander maintenant: Achetez vos kamagra medicaments – kamagra oral jelly
Kamagra Commander maintenant: Kamagra pharmacie en ligne – achat kamagra
http://tadalmed.com/# Tadalafil sans ordonnance en ligne
trouver un mГ©dicament en pharmacie: Pharmacie en ligne France – pharmacie en ligne avec ordonnance pharmafst.com
pharmacie en ligne france livraison belgique: Pharmacie en ligne France – pharmacies en ligne certifiГ©es pharmafst.com
Cialis en ligne: cialis prix – Acheter Cialis 20 mg pas cher tadalmed.shop
pharmacie en ligne france livraison belgique: Livraison rapide – pharmacie en ligne livraison europe pharmafst.com
Kamagra Oral Jelly pas cher [url=https://kamagraprix.shop/#]kamagra 100mg prix[/url] kamagra oral jelly
https://kamagraprix.shop/# Kamagra pharmacie en ligne
Acheter Kamagra site fiable: kamagra oral jelly – Kamagra Commander maintenant
cialis generique: Cialis sans ordonnance 24h – Cialis sans ordonnance 24h tadalmed.shop
Tadalafil 20 mg prix sans ordonnance: Acheter Cialis 20 mg pas cher – Cialis sans ordonnance 24h tadalmed.shop
Pharmacie en ligne livraison Europe [url=https://pharmafst.shop/#]trouver un mГ©dicament en pharmacie[/url] pharmacie en ligne pharmafst.shop
canadian drug: Express Rx Canada – canada drugs online
Rx Express Mexico: RxExpressMexico – mexican online pharmacy
medicine in mexico pharmacies: RxExpressMexico – RxExpressMexico
https://medicinefromindia.com/# medicine courier from India to USA
RxExpressMexico [url=https://rxexpressmexico.com/#]mexico pharmacies prescription drugs[/url] Rx Express Mexico
safe canadian pharmacies: Express Rx Canada – canada rx pharmacy world
indian pharmacy online shopping: medicine courier from India to USA – indian pharmacy
mexican online pharmacy: mexico pharmacies prescription drugs – Rx Express Mexico
http://rxexpressmexico.com/# mexico pharmacy order online
Rx Express Mexico: mexico pharmacy order online – Rx Express Mexico
Rx Express Mexico: mexico pharmacy order online – mexico drug stores pharmacies
medicine courier from India to USA [url=https://medicinefromindia.shop/#]medicine courier from India to USA[/url] MedicineFromIndia
mexico pharmacies prescription drugs: Rx Express Mexico – mexico drug stores pharmacies
http://rxexpressmexico.com/# mexico pharmacies prescription drugs
canadian online pharmacy reviews: Canadian pharmacy shipping to USA – online canadian pharmacy
best canadian online pharmacy: canadian pharmacy world reviews – reputable canadian online pharmacy
indian pharmacy online shopping [url=https://medicinefromindia.com/#]Medicine From India[/url] indian pharmacy online shopping
Rx Express Mexico: Rx Express Mexico – mexico pharmacies prescription drugs
prescription drugs canada buy online: ExpressRxCanada – canada drug pharmacy
medicine courier from India to USA: medicine courier from India to USA – Medicine From India
online pharmacy canada [url=http://expressrxcanada.com/#]Express Rx Canada[/url] reputable canadian online pharmacy
https://rxexpressmexico.shop/# Rx Express Mexico
mexico drug stores pharmacies: mexico drug stores pharmacies – RxExpressMexico
MedicineFromIndia: MedicineFromIndia – Medicine From India
https://expressrxcanada.com/# cheapest pharmacy canada
cheap canadian pharmacy: Express Rx Canada – canada drugstore pharmacy rx
mexican online pharmacy [url=https://rxexpressmexico.shop/#]best online pharmacies in mexico[/url] mexican online pharmacy
legit canadian pharmacy: ExpressRxCanada – canadian pharmacy ed medications
Medicine From India: indian pharmacy online – Medicine From India
https://medicinefromindia.com/# Medicine From India
indian pharmacy: indian pharmacy online shopping – indian pharmacy
canadian online pharmacy: canada pharmacy online – canadian pharmacy 365
certified canadian pharmacy [url=http://expressrxcanada.com/#]canadian pharmacies compare[/url] canadian pharmacy in canada
indian pharmacy online shopping: indian pharmacy online shopping – indian pharmacy online
https://expressrxcanada.com/# canadian pharmacy meds
MedicineFromIndia: medicine courier from India to USA – indianpharmacy com
Rx Express Mexico [url=http://rxexpressmexico.com/#]mexico drug stores pharmacies[/url] mexico pharmacies prescription drugs
indian pharmacy online: pharmacy website india – indian pharmacy paypal
MedicineFromIndia: pharmacy website india – Medicine From India
https://pinuprus.pro/# пинап казино
pin up casino: pin up az – pin up
pin up: pin up – pin-up casino giris
вавада [url=https://vavadavhod.tech/#]вавада казино[/url] vavada casino
вавада официальный сайт: вавада зеркало – vavada casino
pin up вход: пин ап казино официальный сайт – пин ап казино
vavada вход [url=http://vavadavhod.tech/#]vavada casino[/url] вавада казино
https://vavadavhod.tech/# vavada вход
pin-up: pin up azerbaycan – pin up
вавада официальный сайт [url=http://vavadavhod.tech/#]вавада[/url] вавада казино
https://pinupaz.top/# pin up az
pin-up casino giris: pin up – pin up casino
pin up casino: pin up az – pin up casino
https://pinuprus.pro/# пин ап зеркало
vavada вход [url=http://vavadavhod.tech/#]вавада казино[/url] вавада казино
пин ап вход: пинап казино – pin up вход
pin up az: pin up azerbaycan – pin up
pin up: pin up – pin up
пин ап зеркало [url=http://pinuprus.pro/#]пин ап вход[/url] pin up вход
pin up casino: pin-up – pin up az
вавада: вавада зеркало – вавада зеркало
https://pinuprus.pro/# пин ап казино официальный сайт
пин ап зеркало: пинап казино – пинап казино
pin up вход [url=http://pinuprus.pro/#]pin up вход[/url] пин ап вход
вавада: вавада казино – вавада официальный сайт
пинап казино: пин ап казино официальный сайт – пин ап казино официальный сайт
pin up azerbaycan: pinup az – pinup az
http://pinuprus.pro/# пин ап зеркало
vavada вход: вавада зеркало – vavada
вавада казино [url=http://vavadavhod.tech/#]vavada casino[/url] vavada casino
pin up azerbaycan: pinup az – pin up az
пинап казино: пин ап казино официальный сайт – пин ап казино официальный сайт
http://vavadavhod.tech/# вавада официальный сайт
pin up az: pin up – pin up
pin up azerbaycan [url=http://pinupaz.top/#]pinup az[/url] pin up az
vavada: vavada вход – vavada
http://pinuprus.pro/# пин ап зеркало
vavada: вавада казино – vavada вход
пин ап казино: пин ап вход – пин ап казино официальный сайт
пин ап казино [url=http://pinuprus.pro/#]пинап казино[/url] пинап казино
вавада: vavada вход – вавада казино
http://pinupaz.top/# pin up azerbaycan
pinup az: pin up – pinup az
pin-up casino giris: pin up az – pin up
pin up [url=http://pinupaz.top/#]pinup az[/url] pinup az
пин ап казино официальный сайт: пин ап казино официальный сайт – пинап казино
вавада зеркало: vavada – vavada вход
вавада: вавада официальный сайт – вавада казино
vavada: вавада казино – вавада
pin up casino [url=https://pinupaz.top/#]pin up az[/url] pin up az
https://pinuprus.pro/# pin up вход
пинап казино: пин ап вход – пин ап вход
vavada вход: vavada casino – vavada вход
вавада казино: vavada – вавада зеркало
pin up casino [url=https://pinupaz.top/#]pin up[/url] pin-up casino giris
http://vavadavhod.tech/# vavada casino
пин ап вход: пин ап зеркало – pin up вход
вавада: вавада официальный сайт – вавада казино
пин ап казино официальный сайт: пинап казино – пин ап казино
http://vavadavhod.tech/# вавада официальный сайт
vavada casino [url=https://vavadavhod.tech/#]вавада зеркало[/url] вавада казино
pin up az: pin up az – pin-up
вавада: вавада официальный сайт – вавада
https://pinuprus.pro/# пин ап зеркало
пин ап зеркало [url=http://pinuprus.pro/#]пин ап вход[/url] пин ап вход
pinup az: pin-up casino giris – pin-up casino giris
vavada: vavada casino – вавада зеркало
вавада официальный сайт [url=http://vavadavhod.tech/#]вавада официальный сайт[/url] вавада
вавада: вавада зеркало – вавада зеркало
vavada вход: вавада зеркало – вавада казино
https://pinupaz.top/# pin up casino
пин ап казино: пин ап казино официальный сайт – пин ап казино официальный сайт
пин ап казино официальный сайт [url=https://pinuprus.pro/#]пин ап зеркало[/url] пинап казино
https://vavadavhod.tech/# вавада казино
vavada casino: vavada casino – вавада
http://pinuprus.pro/# пин ап казино
вавада казино: вавада зеркало – vavada вход
пин ап казино: пин ап вход – пин ап казино
пин ап зеркало [url=http://pinuprus.pro/#]пинап казино[/url] pin up вход
http://vavadavhod.tech/# вавада официальный сайт
pin up вход: pin up вход – pin up вход
вавада казино: vavada – vavada
pin up вход [url=http://pinuprus.pro/#]pin up вход[/url] пинап казино
http://vavadavhod.tech/# вавада
вавада: вавада официальный сайт – вавада официальный сайт
pin up casino: pin-up – pin up az
vavada casino [url=https://vavadavhod.tech/#]вавада официальный сайт[/url] вавада официальный сайт
http://pinuprus.pro/# пинап казино
vavada вход: vavada вход – vavada
pin-up: pin-up casino giris – pin up azerbaycan
pin up az [url=http://pinupaz.top/#]pin-up[/url] pin up
https://pinuprus.pro/# пинап казино
пин ап казино: пин ап казино – пин ап вход
пин ап зеркало [url=https://pinuprus.pro/#]пинап казино[/url] пин ап казино
http://vavadavhod.tech/# vavada
pin up azerbaycan: pin up casino – pin up
vavada вход: вавада зеркало – vavada вход
pin-up [url=http://pinupaz.top/#]pinup az[/url] pin-up casino giris
https://pinuprus.pro/# пин ап вход
pin up az: pin-up casino giris – pin-up
пин ап зеркало: пинап казино – пин ап вход
pinup az [url=http://pinupaz.top/#]pin-up[/url] pin up casino
pin up az: pin up azerbaycan – pinup az
https://vavadavhod.tech/# вавада зеркало
pin-up casino giris: pin-up – pin up azerbaycan
pinup az [url=https://pinupaz.top/#]pin up casino[/url] pinup az
pin up вход: пин ап вход – pin up вход
http://pinuprus.pro/# пин ап вход
пин ап казино официальный сайт: пин ап казино – пин ап вход
вавада официальный сайт [url=http://vavadavhod.tech/#]vavada[/url] вавада официальный сайт
vavada: vavada casino – вавада зеркало
https://pinupaz.top/# pin up casino
пин ап казино официальный сайт [url=http://pinuprus.pro/#]пин ап казино[/url] пинап казино
вавада официальный сайт: вавада зеркало – vavada вход
http://vavadavhod.tech/# вавада зеркало
вавада зеркало: vavada – вавада казино
pin up azerbaycan [url=http://pinupaz.top/#]pin-up[/url] pin-up
вавада зеркало: вавада официальный сайт – вавада официальный сайт
http://vavadavhod.tech/# vavada вход
pinup az: pin-up – pin-up
pin up azerbaycan [url=https://pinupaz.top/#]pin-up[/url] pin up azerbaycan
вавада казино: вавада зеркало – вавада
https://vavadavhod.tech/# vavada вход
пин ап казино: пин ап казино официальный сайт – pin up вход
пин ап вход [url=https://pinuprus.pro/#]пин ап зеркало[/url] пинап казино
http://pinupaz.top/# pin up casino
вавада официальный сайт: вавада официальный сайт – вавада
Тележка с подъемной платформой предназначена для работы в складских помещениях, производственных предприятий для транспортировки коробок, инструментов и других грузов. Способны поднимать и перемещать грузы весом до 0,5т на высоту до 1500мм.
Высота подъёма: 450-1500 мм.
В качестве защиты от раздавливания подъемный стол оснащен кромкой безопасности, расположенной под наружными краями платформы. При активации она прекращает опускание. Для продолжения опускания платформа должна быть поднята для сброса защиты.
Получить коммерческое предложение:
Надежный гидроцилиндр обеспечивает плавный подъем.
Опыт разработки и производства гидравлических подъемных столов более 50 лет!
pin up casino: pin up azerbaycan – pin up casino
вавада официальный сайт [url=https://vavadavhod.tech/#]вавада казино[/url] вавада официальный сайт
https://pinuprus.pro/# пин ап казино
pin-up casino giris: pin up casino – pin-up
пинап казино: пин ап казино – пин ап казино
http://pinuprus.pro/# пин ап зеркало
pin up [url=http://pinupaz.top/#]pin up az[/url] pin up azerbaycan
pin-up casino giris: pinup az – pin up az
https://vavadavhod.tech/# vavada
pin up вход: pin up вход – пин ап казино официальный сайт
vavada вход [url=http://vavadavhod.tech/#]вавада официальный сайт[/url] вавада официальный сайт
vavada: вавада – vavada вход
http://vavadavhod.tech/# вавада казино
pin up azerbaycan: pin up – pin up azerbaycan
pin up [url=https://pinupaz.top/#]pin-up casino giris[/url] pin up casino
https://vavadavhod.tech/# вавада официальный сайт
pin up вход: пин ап казино – пин ап казино официальный сайт
вавада зеркало [url=http://vavadavhod.tech/#]вавада официальный сайт[/url] vavada casino
вавада официальный сайт: vavada casino – vavada
http://pinuprus.pro/# пин ап казино
vavada вход: vavada вход – vavada вход
pinup az [url=https://pinupaz.top/#]pin up casino[/url] pin up azerbaycan
pinup az: pin-up – pin up az
http://vavadavhod.tech/# vavada casino
pin up az: pin-up – pin up casino
generic tadalafil [url=http://zipgenericmd.com/#]affordable ED medication[/url] cheap Cialis online
trusted Viagra suppliers: Viagra without prescription – best price for Viagra
http://zipgenericmd.com/# affordable ED medication
order Viagra discreetly: fast Viagra delivery – Viagra without prescription
secure checkout ED drugs: reliable online pharmacy Cialis – secure checkout ED drugs
verified Modafinil vendors [url=https://modafinilmd.store/#]buy modafinil online[/url] verified Modafinil vendors
fast Viagra delivery: safe online pharmacy – fast Viagra delivery
buy generic Viagra online: generic sildenafil 100mg – buy generic Viagra online
http://maxviagramd.com/# secure checkout Viagra
modafinil pharmacy: buy modafinil online – safe modafinil purchase
buy modafinil online: modafinil legality – legal Modafinil purchase
order Cialis online no prescription: order Cialis online no prescription – order Cialis online no prescription
discreet shipping [url=http://maxviagramd.com/#]fast Viagra delivery[/url] best price for Viagra
http://modafinilmd.store/# legal Modafinil purchase
modafinil 2025: doctor-reviewed advice – buy modafinil online
trusted Viagra suppliers: order Viagra discreetly – order Viagra discreetly
Viagra without prescription: legit Viagra online – secure checkout Viagra
generic tadalafil: secure checkout ED drugs – affordable ED medication
buy generic Viagra online: generic sildenafil 100mg – buy generic Viagra online
Cialis without prescription: affordable ED medication – secure checkout ED drugs
doctor-reviewed advice [url=https://modafinilmd.store/#]modafinil pharmacy[/url] verified Modafinil vendors
https://maxviagramd.shop/# order Viagra discreetly
buy generic Cialis online: best price Cialis tablets – Cialis without prescription
same-day Viagra shipping: no doctor visit required – safe online pharmacy
best price Cialis tablets: buy generic Cialis online – buy generic Cialis online
order Cialis online no prescription [url=https://zipgenericmd.shop/#]secure checkout ED drugs[/url] online Cialis pharmacy
no doctor visit required: secure checkout Viagra – order Viagra discreetly
FDA approved generic Cialis: Cialis without prescription – Cialis without prescription
https://maxviagramd.com/# safe online pharmacy
generic sildenafil 100mg: secure checkout Viagra – same-day Viagra shipping
cheap Viagra online [url=http://maxviagramd.com/#]fast Viagra delivery[/url] legit Viagra online
modafinil 2025: modafinil legality – modafinil pharmacy
buy modafinil online: modafinil 2025 – safe modafinil purchase
https://maxviagramd.shop/# no doctor visit required
online Cialis pharmacy: reliable online pharmacy Cialis – reliable online pharmacy Cialis
reliable online pharmacy Cialis: online Cialis pharmacy – Cialis without prescription
secure checkout ED drugs [url=https://zipgenericmd.com/#]secure checkout ED drugs[/url] discreet shipping ED pills
modafinil 2025: modafinil 2025 – modafinil legality
https://maxviagramd.shop/# same-day Viagra shipping
purchase Modafinil without prescription: buy modafinil online – verified Modafinil vendors
best price for Viagra: best price for Viagra – secure checkout Viagra
same-day Viagra shipping [url=https://maxviagramd.shop/#]generic sildenafil 100mg[/url] cheap Viagra online
modafinil pharmacy: modafinil pharmacy – verified Modafinil vendors
http://zipgenericmd.com/# online Cialis pharmacy
purchase Modafinil without prescription: purchase Modafinil without prescription – modafinil legality
affordable ED medication [url=http://zipgenericmd.com/#]online Cialis pharmacy[/url] cheap Cialis online
http://zipgenericmd.com/# cheap Cialis online
online Cialis pharmacy: FDA approved generic Cialis – discreet shipping ED pills
no doctor visit required: safe online pharmacy – no doctor visit required
order Cialis online no prescription [url=https://zipgenericmd.shop/#]affordable ED medication[/url] reliable online pharmacy Cialis
trusted Viagra suppliers: discreet shipping – safe online pharmacy
https://modafinilmd.store/# modafinil legality
order Cialis online no prescription: buy generic Cialis online – order Cialis online no prescription
FDA approved generic Cialis: reliable online pharmacy Cialis – reliable online pharmacy Cialis
secure checkout Viagra [url=http://maxviagramd.com/#]legit Viagra online[/url] discreet shipping
legit Viagra online: order Viagra discreetly – generic sildenafil 100mg
http://modafinilmd.store/# Modafinil for sale
trusted Viagra suppliers: Viagra without prescription – fast Viagra delivery
order prednisone 10mg: prednisone 30 mg coupon – PredniHealth
prednisone for sale in canada: PredniHealth – prednisone uk price
https://amohealthcare.store/# Amo Health Care
prednisone medicine: PredniHealth – prednisone pack
azithromycin amoxicillin: order amoxicillin online – buy amoxil
amoxicillin 500mg buy online uk [url=https://amohealthcare.store/#]how to get amoxicillin[/url] Amo Health Care
Amo Health Care: Amo Health Care – Amo Health Care
https://prednihealth.com/# 5 prednisone in mexico
Amo Health Care: Amo Health Care – Amo Health Care
where buy cheap clomid without insurance: can you buy generic clomid – where to get generic clomid
PredniHealth: PredniHealth – PredniHealth
generic clomid without dr prescription [url=http://clomhealth.com/#]Clom Health[/url] where to buy cheap clomid online
https://clomhealth.com/# cost cheap clomid online
prednisone 5 mg tablet: PredniHealth – PredniHealth
get cheap clomid without dr prescription: order clomid price – generic clomid without insurance
Amo Health Care: Amo Health Care – Amo Health Care
amoxicillin 250 mg capsule [url=https://amohealthcare.store/#]Amo Health Care[/url] Amo Health Care
https://amohealthcare.store/# amoxicillin 500mg buy online canada
cost of amoxicillin 30 capsules: Amo Health Care – amoxicillin over counter
amoxicillin 750 mg price: amoxicillin 500mg – Amo Health Care
purchase amoxicillin 500 mg: Amo Health Care – amoxicillin 500 tablet
Amo Health Care [url=https://amohealthcare.store/#]can you buy amoxicillin over the counter in canada[/url] Amo Health Care
https://clomhealth.com/# can i order clomid for sale
prednisone 10mg tabs: how much is prednisone 10 mg – 54 prednisone
prednisone 60 mg tablet: prednisone uk – PredniHealth
https://clomhealth.com/# can i purchase generic clomid online
prednisone over the counter uk [url=https://prednihealth.com/#]PredniHealth[/url] prednisone 4mg tab
Amo Health Care: Amo Health Care – amoxicillin generic
Amo Health Care: amoxicillin without a prescription – generic amoxicillin over the counter
https://amohealthcare.store/# generic amoxicillin
where to buy amoxicillin pharmacy [url=https://amohealthcare.store/#]order amoxicillin 500mg[/url] Amo Health Care
amoxicillin 500mg prescription: amoxicillin 500 mg brand name – Amo Health Care
order generic clomid without insurance: Clom Health – cost cheap clomid without dr prescription
https://prednihealth.com/# order prednisone 10mg
cialis drug: TadalAccess – super cialis
cialis alcohol: cialis for daily use cost – cialis review
https://tadalaccess.com/# cheap cialis free shipping
tadalafil best price 20 mg [url=https://tadalaccess.com/#]TadalAccess[/url] purchasing cialis
cialis for sale in toront ontario: tadalafil and voice problems – where to get the best price on cialis
sunrise pharmaceutical tadalafil: Tadal Access – tadalafil citrate research chemical
https://tadalaccess.com/# cialis 20 mg tablets and prices
when will generic cialis be available [url=https://tadalaccess.com/#]tadalafil liquid review[/url] order generic cialis online 20 mg 20 pills
tadalafil review forum: Tadal Access – cialis professional review
tadalafil pulmonary hypertension: TadalAccess – tadalafil 5mg generic from us
https://tadalaccess.com/# whats the max safe dose of tadalafil xtenda for a healthy man
cialis and melanoma: tadalafil 20mg canada – tadalafil generic headache nausea
cialis pills for sale [url=https://tadalaccess.com/#]tadalafil 20 mg directions[/url] cialis definition
no prescription female cialis: buy cialis online in austalia – natural alternative to cialis
https://tadalaccess.com/# buy cialis canadian
cialis online without pres: cialis generic best price – cialis generic
buy cialis on line: cialis liquid for sale – where can i get cialis
tadalafil and ambrisentan newjm 2015 [url=https://tadalaccess.com/#]generic cialis from india[/url] generic cialis vs brand cialis reviews
https://tadalaccess.com/# buy cialis on line
benefits of tadalafil over sidenafil: side effects of cialis – cialis online paypal
best time to take cialis 5mg: TadalAccess – buy voucher for cialis daily online
price of cialis in pakistan [url=https://tadalaccess.com/#]TadalAccess[/url] cialis generic name
https://tadalaccess.com/# buy tadalafil cheap
cialis australia online shopping: Tadal Access – peptide tadalafil reddit
cialis sales in victoria canada: TadalAccess – where to get generic cialis without prescription
Преимущества подъемных столов.
Подъёмные столы NOBLELIFT.
Арт. 700058.
To view this video please enable JavaScript, and consider upgrading to a web browser that supports HTML5 video.
Цена: 75 840 руб.
Наш большой опыт в проектировании и производстве гарантирует надежность и качество вашего подъемника.
cialis super active plus [url=https://tadalaccess.com/#]cialis difficulty ejaculating[/url] compounded tadalafil troche life span
https://tadalaccess.com/# order cialis online no prescription reviews
does tadalafil lower blood pressure: canadian pharmacy cialis 20mg – cialis next day delivery
maximpeptide tadalafil review: side effects of cialis daily – buy liquid cialis online
cialis prescription assistance program [url=https://tadalaccess.com/#]Tadal Access[/url] best place to get cialis without pesricption
https://tadalaccess.com/# cialis with dapoxetine
cialis 20 mg coupon: mail order cialis – cialis and adderall
how long does cialis last in your system: free coupon for cialis – cialis generic purchase
https://tadalaccess.com/# cialis slogan
20 mg tadalafil best price [url=https://tadalaccess.com/#]Tadal Access[/url] canadian pharmacy generic cialis
buy generic cialis: Tadal Access – cialis 5mg daily how long before it works
is there a generic cialis available: cialis before and after pictures – cialis meme
https://tadalaccess.com/# cialis mechanism of action
tadalafil dose for erectile dysfunction [url=https://tadalaccess.com/#]cialis uses[/url] side effects of cialis
buy cheap cialis online with mastercard: cialis generic overnite – average dose of tadalafil
what is the use of tadalafil tablets: TadalAccess – purchase cialis online cheap
https://tadalaccess.com/# cheap generic cialis canada
cialis for pulmonary hypertension [url=https://tadalaccess.com/#]Tadal Access[/url] tadalafil liquid fda approval date
cialis strength: Tadal Access – cialis indien bezahlung mit paypal
buy tadalafil online paypal: TadalAccess – shop for cialis
https://tadalaccess.com/# cialis covered by insurance
tadalafil (exilar-sava healthcare) [generic version of cialis] (rx) lowest price [url=https://tadalaccess.com/#]TadalAccess[/url] when will cialis be over the counter
cialis generic overnite: Tadal Access – cialis online no prescription australia
https://tadalaccess.com/# buy cialis by paypal
cialis for daily use side effects: what are the side effect of cialis – cialis samples
what happens if you take 2 cialis: Tadal Access – what to do when cialis stops working
cialis generic release date [url=https://tadalaccess.com/#]buying cialis[/url] tadalafil 20mg
https://tadalaccess.com/# cialis free trial phone number
tadalafil daily use: TadalAccess – where to buy tadalafil in singapore
tadalafil 40 mg with dapoxetine 60 mg: cialis free trial voucher – cialis manufacturer
generic cialis available in canada [url=https://tadalaccess.com/#]TadalAccess[/url] order cialis from canada
https://tadalaccess.com/# cialis 20 mg price walmart
pastillas cialis: letairis and tadalafil – tadalafil generic 20 mg ebay
cialis online paypal: Tadal Access – when will cialis be generic
tadalafil tablets side effects [url=https://tadalaccess.com/#]Tadal Access[/url] cialis payment with paypal
https://tadalaccess.com/# cialis sample pack
tadalafil best price 20 mg: cialis drug – best price for cialis
buy tadalafil online paypal: Tadal Access – cialis discount card
what is the difference between cialis and tadalafil [url=https://tadalaccess.com/#]Tadal Access[/url] tadalafil lowest price
https://tadalaccess.com/# cialis wikipedia
cialis 100mg from china: where to buy cialis cheap – cialis 100mg from china
cialis review: tadalafil online paypal – cialis doesnt work
cialis prescription cost [url=https://tadalaccess.com/#]cialis price cvs[/url] cialis from canadian pharmacy registerd
https://tadalaccess.com/# what does cialis do
cialis 50mg: cialis prices in mexico – is there a generic cialis available in the us
cialis 20 mg best price: tadalafil soft tabs – cialis for sale over the counter
https://tadalaccess.com/# cialis dapoxetine overnight shipment
cialis generic overnite [url=https://tadalaccess.com/#]best price on cialis[/url] cialis headache
when should i take cialis: cialis canada price – cheap cialis by post
what does cialis look like: buying cialis generic – when to take cialis 20mg
https://tadalaccess.com/# cialis 30 mg dose
cialis manufacturer coupon [url=https://tadalaccess.com/#]cialis using paypal in australia[/url] snorting cialis
cheap cialis 20mg: TadalAccess – adcirca tadalafil
cialis 50mg: TadalAccess – cialis patent expiration date
https://tadalaccess.com/# tadalafil citrate powder
cialis 5mg price comparison [url=https://tadalaccess.com/#]Tadal Access[/url] snorting cialis
cialis black 800 to buy in the uk one pill: Tadal Access – online cialis prescription
cialis online pharmacy australia: TadalAccess – canada drugs cialis
https://tadalaccess.com/# letairis and tadalafil
tadalafil buy online canada: cialis payment with paypal – cialis how to use
cialis buy online [url=https://tadalaccess.com/#]Tadal Access[/url] no presciption cialis
generic cialis 5mg: TadalAccess – cialis online no prior prescription
https://tadalaccess.com/# is generic cialis available in canada
cialis side effects with alcohol: TadalAccess – cialis bodybuilding
cheap cialis dapoxitine cheap online [url=https://tadalaccess.com/#]natural cialis[/url] where can i buy cialis online in australia
https://tadalaccess.com/# cialis overnight shipping
tadalafil (exilar-sava healthcare) [generic version of cialis] (rx) lowest price: safest and most reliable pharmacy to buy cialis – cialis and grapefruit enhance
cialis 20 mg: Tadal Access – cialis buy australia online
tadalafil 40 mg india [url=https://tadalaccess.com/#]tadalafil daily use[/url] snorting cialis
https://tadalaccess.com/# cialis vs tadalafil
cialis prices in mexico: TadalAccess – cialis store in philippines
cialis experience: Tadal Access – how long does cialis take to work 10mg
cialis online paypal [url=https://tadalaccess.com/#]TadalAccess[/url] cialis purchase canada
cialis samples: stockists of cialis – stockists of cialis
whats cialis: generic cialis super active tadalafil 20mg – cialis generic canada
cialis mechanism of action [url=https://tadalaccess.com/#]Tadal Access[/url] can you drink wine or liquor if you took in tadalafil
https://tadalaccess.com/# cialis back pain
cialis price cvs: TadalAccess – where can i get cialis
brand cialis: TadalAccess – canadian online pharmacy cialis
cialis before and after [url=https://tadalaccess.com/#]cialis 30 mg dose[/url] tadalafil price insurance
https://tadalaccess.com/# cialis patent
buy cialis 20mg: is tadalafil available at cvs – tadalafil tablets 20 mg reviews
online cialis australia: cialis 2.5 mg – achats produit tadalafil pour femme en ligne
cialis in canada [url=https://tadalaccess.com/#]online cialis prescription[/url] cialis soft
https://tadalaccess.com/# cialis advertisement
active ingredient in cialis: cialis 20mg review – how long does cialis last 20 mg
buy cialis online reddit: buy cialis cheap fast delivery – buy cialis online usa
how to buy tadalafil online [url=https://tadalaccess.com/#]Tadal Access[/url] find tadalafil
https://tadalaccess.com/# cialis reddit
price of cialis at walmart: cialis 800 black canada – cialis genetic
cialis contraindications: pastilla cialis – cialis price costco
buy tadalafil cheap online: Tadal Access – cialis goodrx
is tadalafil and cialis the same thing? [url=https://tadalaccess.com/#]Tadal Access[/url] tadalafil generic usa
https://tadalaccess.com/# cialis samples for physicians
cialis prices at walmart: TadalAccess – cialis professional ingredients
buy cialis no prescription australia: mantra 10 tadalafil tablets – no prescription tadalafil
safest and most reliable pharmacy to buy cialis [url=https://tadalaccess.com/#]cialis cost at cvs[/url] cialis vs flomax for bph
https://tadalaccess.com/# sildalis sildenafil tadalafil
cialis side effects: Tadal Access – cialis for sale
cialis free sample [url=https://tadalaccess.com/#]Tadal Access[/url] cialis bathtub
cialis for daily use reviews: Tadal Access – generic cialis 20 mg from india
https://tadalaccess.com/# cialis online usa
prescription for cialis: Tadal Access – what is the generic name for cialis
buy cialis canada paypal [url=https://tadalaccess.com/#]Tadal Access[/url] cialis online no prior prescription
max dosage of cialis: cialis tadalafil discount – what happens if you take 2 cialis
https://tadalaccess.com/# order generic cialis online 20 mg 20 pills
cialis online paypal [url=https://tadalaccess.com/#]vidalista 20 tadalafil tablets[/url] over the counter drug that works like cialis
what is cialis used for: no prescription female cialis – cheap cialis pills uk
https://tadalaccess.com/# how to buy tadalafil
cialis and adderall [url=https://tadalaccess.com/#]Tadal Access[/url] cialis side effects forum
cialis buy: Tadal Access – is cialis a controlled substance
https://tadalaccess.com/# cialis for sale brand
buy cialis online usa: vardenafil and tadalafil – cialis over the counter in spain
buy cialis on line [url=https://tadalaccess.com/#]TadalAccess[/url] tadalafil review forum
buy cialis online free shipping: cialis canada online – cialis for prostate
https://tadalaccess.com/# sildalis sildenafil tadalafil
cialis time [url=https://tadalaccess.com/#]cialis side effect[/url] how long before sex should you take cialis
purchase cialis online: TadalAccess – cialis high blood pressure
https://tadalaccess.com/# tadalafil liquid review
cialis as generic: peptide tadalafil reddit – cialis online no prescription australia
does cialis really work [url=https://tadalaccess.com/#]TadalAccess[/url] cialis when to take
https://tadalaccess.com/# cialis generic overnite
cheap cialis pills uk: cialis canada online – cialis tadalafil cheapest online
what are the side effects of cialis [url=https://tadalaccess.com/#]TadalAccess[/url] cialis coupon rite aid
does tadalafil work: generic tadalafil canada – cialis reviews
cialis canadian pharmacy [url=https://tadalaccess.com/#]TadalAccess[/url] cialis with out a prescription
https://tadalaccess.com/# cialis com free sample
cialis pills online: TadalAccess – teva generic cialis
cialis side effects with alcohol [url=https://tadalaccess.com/#]TadalAccess[/url] cialis goodrx
Устройство передвижного подъемного стола.
Арт. Артикул 67-5005.
Доп. скидка 5% на всю технику Smartlift из наличия до 15.04, суммируется с акциями, применяется автоматически (заказ через корзину) или менеджером (заказ по телефону, Email или в форме).
Передвижной подъемный стол является оборудованием для поднятия и перемещения груза. Устройство представляет специальную платформу, на которой поднимаются различные предметы при помощи ножничного механизма. Тележка с подъемной платформой часто применяются при выполнении сборочных, погрузочно-разгрузочных операций на производстве, на складах, стройках, в автосервисах. Тележки с подъемом используется в производственных цехах, на складах и торговых объектах, в мастерских и автосервисах. Они предназначены для облегчения работы с грузами в различной упаковке (таре): в ящиках, мешках, рулонах. Также применяются при выполнении сборочных, погрузочно-разгрузочных операций. Стол позволяет сравнять груз на уровне рабочего механизма и поддерживать технологический процесс.
Собственный вес: 160 кг.
Подъемники паллет.
get antibiotics without seeing a doctor: Biot Pharm – buy antibiotics over the counter
get antibiotics quickly: BiotPharm – buy antibiotics
buy antibiotics over the counter: BiotPharm – best online doctor for antibiotics
Buy medicine online Australia [url=http://pharmau24.com/#]PharmAu24[/url] Buy medicine online Australia
antibiotic without presription: buy antibiotics online uk – get antibiotics quickly
ed medications cost: online ed medication – boner pills online
https://pharmau24.com/# Online medication store Australia
antibiotic without presription: BiotPharm – best online doctor for antibiotics
Discount pharmacy Australia: Online medication store Australia – Discount pharmacy Australia
Over the counter antibiotics for infection [url=https://biotpharm.com/#]buy antibiotics online uk[/url] Over the counter antibiotics pills
online ed medicine: best online ed treatment – online erectile dysfunction
over the counter antibiotics: BiotPharm – get antibiotics quickly
https://eropharmfast.shop/# erectile dysfunction pills online
get antibiotics quickly: buy antibiotics online – antibiotic without presription
get ed meds online: get ed prescription online – Ero Pharm Fast
https://biotpharm.com/# buy antibiotics over the counter
buy antibiotics over the counter: Biot Pharm – buy antibiotics for uti
best ed medication online [url=https://eropharmfast.com/#]Ero Pharm Fast[/url] Ero Pharm Fast
Over the counter antibiotics pills: buy antibiotics from india – buy antibiotics from canada
http://biotpharm.com/# buy antibiotics
Ero Pharm Fast: Ero Pharm Fast – Ero Pharm Fast
get antibiotics without seeing a doctor [url=https://biotpharm.com/#]Biot Pharm[/url] Over the counter antibiotics for infection
Medications online Australia: Medications online Australia – pharmacy online australia
pharmacy online australia: Buy medicine online Australia – Online medication store Australia
pharmacy online australia: online pharmacy australia – Pharm Au24
http://biotpharm.com/# buy antibiotics
Ero Pharm Fast [url=https://eropharmfast.com/#]erectile dysfunction medicine online[/url] Ero Pharm Fast
Ero Pharm Fast: buy ed meds online – ed drugs online
how to get ed pills: Ero Pharm Fast – buy erectile dysfunction treatment
Over the counter antibiotics for infection: buy antibiotics online – Over the counter antibiotics pills
over the counter antibiotics [url=https://biotpharm.shop/#]antibiotic without presription[/url] buy antibiotics from india
https://eropharmfast.com/# cheap ed meds online
cheap ed: Ero Pharm Fast – online erectile dysfunction prescription
buy antibiotics over the counter [url=http://biotpharm.com/#]BiotPharm[/url] best online doctor for antibiotics
Pharm Au 24: Discount pharmacy Australia – Online medication store Australia
ed rx online [url=https://eropharmfast.shop/#]ed rx online[/url] online erectile dysfunction medication
http://pharmau24.com/# Pharm Au 24
where to buy erectile dysfunction pills: ed meds on line – where to get ed pills
low cost ed pills [url=https://eropharmfast.shop/#]ed online prescription[/url] ed prescriptions online
buy antibiotics from canada: cheapest antibiotics – get antibiotics without seeing a doctor
ed medication online [url=https://eropharmfast.com/#]Ero Pharm Fast[/url] cheap erectile dysfunction pills
Pharm Au24: Buy medicine online Australia – Pharm Au 24
https://pharmau24.shop/# Medications online Australia
Ero Pharm Fast [url=https://eropharmfast.shop/#]best ed medication online[/url] discount ed pills
cheapest ed medication: best online ed treatment – Ero Pharm Fast
ed medication online [url=https://eropharmfast.com/#]Ero Pharm Fast[/url] ed medications online
Online drugstore Australia: Buy medicine online Australia – Online medication store Australia
https://pharmau24.com/# online pharmacy australia
online pharmacy australia [url=http://pharmau24.com/#]Discount pharmacy Australia[/url] pharmacy online australia
Ero Pharm Fast: online ed medication – online erectile dysfunction prescription
pharmacie en ligne sans ordonnance: pharmacie en ligne pas cher – Achat mГ©dicament en ligne fiable
pharmacie en ligne pas cher: pharmacie en ligne sans ordonnance – Pharmacie Internationale en ligne
acheter medicaments sans ordonnance [url=https://pharmsansordonnance.com/#]acheter medicaments sans ordonnance[/url] Achat mГ©dicament en ligne fiable
acheter Viagra sans ordonnance: commander Viagra discretement – viagra sans ordonnance
https://kampascher.shop/# kamagra livraison 24h
viagra sans ordonnance: Meilleur Viagra sans ordonnance 24h – prix bas Viagra générique
Viagra sans ordonnance 24h: Meilleur Viagra sans ordonnance 24h – Viagra vente libre pays
pharmacie en ligne [url=http://pharmsansordonnance.com/#]pharmacie en ligne sans ordonnance[/url] pharmacie en ligne france livraison belgique
Kamagra oral jelly pas cher: acheter Kamagra sans ordonnance – acheter kamagra site fiable
cialis prix: acheter Cialis sans ordonnance – cialis generique
pharmacie en ligne sans ordonnance [url=http://pharmsansordonnance.com/#]pharmacie internet fiable France[/url] pharmacie en ligne france livraison internationale
viagra en ligne: acheter Viagra sans ordonnance – viagra sans ordonnance
viagra en ligne: Meilleur Viagra sans ordonnance 24h – viagra sans ordonnance
http://pharmsansordonnance.com/# vente de mГ©dicament en ligne
Kamagra oral jelly pas cher: acheter kamagra site fiable – kamagra gel
acheter Kamagra sans ordonnance [url=https://kampascher.com/#]kamagra en ligne[/url] kamagra en ligne
livraison discrete Kamagra: livraison discrete Kamagra – achat kamagra
achat kamagra: commander Kamagra en ligne – kamagra oral jelly
Cialis sans ordonnance 24h: Cialis pas cher livraison rapide – traitement ED discret en ligne
Medicaments en ligne livres en 24h: Medicaments en ligne livres en 24h – trouver un mГ©dicament en pharmacie
pharmacie en ligne sans ordonnance [url=https://pharmsansordonnance.shop/#]pharmacie en ligne pas cher[/url] pharmacie en ligne avec ordonnance
http://kampascher.com/# trouver un mГ©dicament en pharmacie
prix bas Viagra générique: Meilleur Viagra sans ordonnance 24h – viagra sans ordonnance
kamagra 100mg prix: kamagra gel – kamagra livraison 24h
trouver un mГ©dicament en pharmacie: pharmacie en ligne sans prescription – Achat mГ©dicament en ligne fiable
prix bas Viagra generique [url=https://viasansordonnance.com/#]prix bas Viagra generique[/url] Meilleur Viagra sans ordonnance 24h
Viagra sans ordonnance 24h Amazon: Meilleur Viagra sans ordonnance 24h – Viagra sans ordonnance 24h
commander Cialis en ligne sans prescription: Acheter Cialis – Acheter Cialis
pharmacie en ligne sans ordonnance: commander sans consultation medicale – pharmacies en ligne certifiГ©es
kamagra pas cher [url=https://kampascher.shop/#]achat kamagra[/url] achat kamagra
http://ciasansordonnance.com/# Cialis sans ordonnance 24h
kamagra livraison 24h: achat kamagra – kamagra livraison 24h
commander Viagra discretement: viagra en ligne – Acheter du Viagra sans ordonnance
Acheter Cialis: Cialis générique sans ordonnance – cialis sans ordonnance
acheter Kamagra sans ordonnance [url=https://kampascher.com/#]Kamagra oral jelly pas cher[/url] kamagra oral jelly
Acheter du Viagra sans ordonnance: acheter Viagra sans ordonnance – commander Viagra discretement
cialis generique: acheter Cialis sans ordonnance – Pharmacie sans ordonnance
viagra en ligne: acheter Viagra sans ordonnance – Viagra sans ordonnance 24h
https://viasansordonnance.shop/# viagra en ligne
commander sans consultation medicale [url=https://pharmsansordonnance.com/#]acheter medicaments sans ordonnance[/url] pharmacie en ligne sans ordonnance
pharmacie en ligne france livraison belgique: Medicaments en ligne livres en 24h – acheter mГ©dicament en ligne sans ordonnance
Cialis sans ordonnance 24h: commander Cialis en ligne sans prescription – commander Cialis en ligne sans prescription
acheter Viagra sans ordonnance: Acheter du Viagra sans ordonnance – prix bas Viagra générique
acheter kamagra site fiable [url=http://kampascher.com/#]Kamagra oral jelly pas cher[/url] kamagra 100mg prix
pharmacie en ligne: Medicaments en ligne livres en 24h – pharmacie en ligne france fiable
commander Cialis en ligne sans prescription: Acheter Cialis – cialis generique
https://kampascher.shop/# kamagra gel
commander Viagra discretement [url=http://viasansordonnance.com/#]acheter Viagra sans ordonnance[/url] acheter Viagra sans ordonnance
kamagra en ligne: pharmacie en ligne – kamagra pas cher
Meilleur Viagra sans ordonnance 24h: Viagra sans ordonnance 24h – Meilleur Viagra sans ordonnance 24h
Acheter du Viagra sans ordonnance: prix bas Viagra generique – livraison rapide Viagra en France
acheter Viagra sans ordonnance [url=https://viasansordonnance.shop/#]commander Viagra discretement[/url] Acheter du Viagra sans ordonnance
commander Cialis en ligne sans prescription: Cialis sans ordonnance 24h – cialis prix
cialis prix: cialis sans ordonnance – Cialis sans ordonnance 24h
https://kampascher.com/# acheter kamagra site fiable
acheter medicaments sans ordonnance [url=http://pharmsansordonnance.com/#]acheter medicaments sans ordonnance[/url] pharmacie en ligne france livraison belgique
commander Viagra discretement: Meilleur Viagra sans ordonnance 24h – Acheter du Viagra sans ordonnance
prix bas Viagra generique: Acheter du Viagra sans ordonnance – prix bas Viagra generique
acheter kamagra site fiable: kamagra livraison 24h – Kamagra oral jelly pas cher
http://pharmsansordonnance.com/# п»їpharmacie en ligne france
kamagra pas cher: achat kamagra – acheter Kamagra sans ordonnance
pharmacie en ligne: acheter medicaments sans ordonnance – pharmacies en ligne certifiГ©es
pharmacie internet fiable France [url=http://pharmsansordonnance.com/#]Pharmacies en ligne certifiees[/url] pharmacie en ligne sans ordonnance
viagra en ligne: acheter Viagra sans ordonnance – Viagra generique en pharmacie
commander Cialis en ligne sans prescription: acheter Cialis sans ordonnance – traitement ED discret en ligne
pharmacie en ligne sans ordonnance [url=https://pharmsansordonnance.com/#]pharmacie en ligne sans prescription[/url] pharmacie en ligne pas cher
pharmacie en ligne france livraison internationale: Acheter Cialis – Cialis pas cher livraison rapide
https://ciasansordonnance.com/# Acheter Cialis
acheter Kamagra sans ordonnance [url=https://kampascher.com/#]achat kamagra[/url] kamagra oral jelly
pharmacie en ligne sans ordonnance: acheter medicaments sans ordonnance – pharmacie en ligne france livraison internationale
pharmacie en ligne pas cher [url=https://pharmsansordonnance.shop/#]Pharmacies en ligne certifiees[/url] Pharmacie sans ordonnance
pharmacie en ligne pas cher: commander sans consultation medicale – trouver un mГ©dicament en pharmacie
Acheter du Viagra sans ordonnance: Viagra sans ordonnance 24h – SildГ©nafil 100 mg prix en pharmacie en France
https://kampascher.shop/# achat kamagra
cialis prix [url=https://ciasansordonnance.com/#]Cialis pas cher livraison rapide[/url] cialis prix
Viagra sans ordonnance 24h: livraison rapide Viagra en France – Viagra sans ordonnance 24h Amazon
Cialis pas cher livraison rapide [url=https://ciasansordonnance.shop/#]Acheter Cialis[/url] commander Cialis en ligne sans prescription
cialis prix: Cialis pas cher livraison rapide – cialis prix
Cialis pas cher livraison rapide [url=http://ciasansordonnance.com/#]traitement ED discret en ligne[/url] Cialis generique sans ordonnance
cialis prix: pharmacie en ligne livraison europe – Cialis generique sans ordonnance
http://pharmsansordonnance.com/# Pharmacie en ligne livraison Europe
Kamagra oral jelly pas cher [url=https://kampascher.com/#]kamagra en ligne[/url] livraison discrete Kamagra
Cialis generique sans ordonnance: Acheter Cialis 20 mg pas cher – commander Cialis en ligne sans prescription
tadalafil 20mg acheter [url=http://pharmacieexpress.com/#]medicament avec ordonnance[/url] prorhinel rhume dosette
donde puedo comprar azitromicina sin receta medica: Confia Pharma – se puede comprar concerta sin receta
http://pharmacieexpress.com/# achat viagra
comprar naproxeno sodico sin receta: Confia Pharma – farmacia online para rumanos
decapeptyl 3.75 prezzo [url=http://farmaciasubito.com/#]Farmacia Subito[/url] farmacia online lombardia
farmacia online legitima: ВїquГ© antibiГіticos puedo comprar sin receta? – mascherine chirurgiche farmacia online
zolpeduar principio attivo [url=http://farmaciasubito.com/#]Farmacia Subito[/url] robilas antistaminico prezzo
puedo comprar viagra sin receta: farmacia badajoz online – puedo comprar amoxicilina sin receta mГ©dica
https://pharmacieexpress.com/# ordonnance par internet
flixotide spray: xatral 10 mg prezzo – cialis 5 mg 28 compresse prezzo
la farmacia online descuento: comprar antalgin sin receta – donde comprar xenical sin receta
pilule sans ordonnance pharmacie [url=https://pharmacieexpress.shop/#]acheter tadalafil en ligne[/url] durex feeling sensual
tecnico auxiliar de farmacia y parafarmacia online: farmacia online gastos envio gratis – comprar cialis online sin receta
https://pharmacieexpress.com/# angine medicament sans ordonnance
muscoril fiale sono mutuabili [url=https://farmaciasubito.shop/#]Farmacia Subito[/url] prezzo augmentin
spirale kyleena: Farmacia Subito – farmacia orlando
colpogyn ovuli: п»їfarmacia online – online farmacia italy
dГіnde comprar sildenafil sin receta [url=https://confiapharma.com/#]se puede comprar miconazol sin receta[/url] la farmacia online mas barata
farmacia online clembuterol: farmacia online peru – comprar cialis en madrid sin receta
acheter viagra homme [url=https://pharmacieexpress.shop/#]medicament infection urinaire sans ordonnance[/url] pharmacie bagnolet
tadalafil arrow sans ordonnance: suprax sans ordonnance en pharmacie – cialis generique 20mg
http://confiapharma.com/# se puede comprar dutasteride sin receta
tavor morte: Farmacia Subito – feldene fiale
farmacia online puglia: comprar tryptizol sin receta – mascarillas fp3 farmacia online
paises donde se puede comprar viagra sin receta [url=http://confiapharma.com/#]Confia Pharma[/url] se puede comprar tobrex sin receta
farmacia online chat: farmacia online trieste – panacef sciroppo alla fragola prezzo
sachet infection urinaire sans ordonnance [url=https://pharmacieexpress.com/#]antibiotique ordonnance[/url] medicament pour maigrir en pharmacie sans ordonnance
cialis prix en pharmacie: Pharmacie Express – prix cialis 5mg
https://farmaciasubito.shop/# farmacia sicura online
farmacia bagnolo cremasco: Farmacia Subito – farmacia shop online recensioni
palexia 50 mg [url=https://farmaciasubito.shop/#]linezolid 600[/url] dottor max farmacia online
como comprar medicamento sin receta: loja farmacia online – farmacia guareГ±a online
dapoxetina se puede comprar sin receta: Confia Pharma – mi farmacia online sin receta preferida
pharmacie sans ordonnance montpellier [url=https://pharmacieexpress.shop/#]cГ©tirizine sans ordonnance prix[/url] sulfur 15ch
opiniones mi farmacia online: Confia Pharma – diane 35 se puede comprar sin receta
rubifen sin receta comprar: master en farmacia hospitalaria online – farmacia barata online cordoba
https://confiapharma.com/# farmacia online alzira
acheter solupred 20 mg sans ordonnance [url=https://pharmacieexpress.shop/#]arnica montana 7 ch[/url] sro sachet
alcion farmaco: medrol a cosa serve – movicol soluzione orale
ketoderm sans ordonnance en pharmacie: infection urinaire femme medicament sans ordonnance – viagra pas cher
comprar wegovy sin receta: Confia Pharma – farmacia online preservativos
cerotti antinfiammatori [url=https://farmaciasubito.shop/#]test hiv farmacia online[/url] punture pappataci immagini
https://confiapharma.shop/# farmacia sarasketa online
coverlam 5/5: sirdalud compresse prezzo – menaderm simplex crema a cosa serve
farmacia genericos comprar cialis generico online tadalafil precio: mascarillas ffp2 comprar online farmacia – el diazepam se puede comprar sin receta?
come far prendere l’antibiotico ai bambini [url=https://farmaciasubito.shop/#]effortil gocce[/url] lyrica prezzo 50 mg
dubine crema a cosa serve: Farmacia Subito – pillola jadiza
farmacia 24 h online: campoamor farmacia online – auxiliar de farmacia y parafarmacia online
farmacia jerez online [url=http://confiapharma.com/#]farmacia online portugal envio a espaГ±a[/url] puedo comprar citalopram sin receta
farmacia santa rita online: Confia Pharma – el sildenafil se puede comprar sin receta
https://pharmacieexpress.com/# melatonine 3 mg en pharmacie sans ordonnance
comprar minoxidil farmacia online: antica farmacia online – puedo comprar anticonceptivos sin receta medica
puedes comprar ibuprofeno sin receta [url=http://confiapharma.com/#]farmacia online test embarazo[/url] farmacia online american express
canigen dhppi/l: giant farmaco – movicol soluzione orale
donde comprar antidepresivos sin receta: farmacia online termometro – farmacia online preguntas
biorinil spray nasale prezzo [url=http://farmaciasubito.com/#]zolpeduar 5 mg effetti collaterali[/url] viagra price
peut on voir un rhumatologue sans ordonnance: ordonnance securisee medecin – ozempic sans ordonnance belgique
farmacia liceo online opiniones: tu farmacia online online – farmacia online san marino
http://pharmacieexpress.com/# ordonnance cholesterol
consultation medecin en ligne ordonnance [url=https://pharmacieexpress.shop/#]cialis sans ordonnance pharmacie france[/url] mГ©dicament pour grossir en pharmacie sans ordonnance
deltacortene per cani: meloxidyl cane – endodien prezzo
http://pharmmex.com/# allergy medicine in mexico
prescriptions from india [url=https://inpharm24.com/#]doctor of pharmacy india[/url] india pharmacy of the world
online medicine order: india prescription drugs – pharmacy from india
mexican medicine cream: Pharm Mex – canadian pharmacies that ship to the us
http://inpharm24.com/# buy medicine online in india
Brand Levitra [url=https://pharmexpress24.shop/#]kroger online pharmacy[/url] viagra pharmacy thailand
sun pharmacy india: online medicine delivery in india – b pharmacy salary in india
online medicine shopping: percocet pharmacy – bupropion pharmacy prices
clozaril registry pharmacy [url=http://pharmexpress24.com/#]Pharm Express 24[/url] diplomat pharmacy lipitor
dulcolax pharmacy: Pharm Express 24 – claritin d online pharmacy
india rx: buy viagra online india – buy viagra online in india
https://pharmmex.com/# mexican pharmacy viagra
mexican online stores: Pharm Mex – mexican packaging
online pharmacy chat: buy cialis cheap us pharmacy – online pharmacy motilium
simvastatin people’s pharmacy [url=https://pharmexpress24.shop/#]boots pharmacy viagra[/url] pharmacy coupons
pharmacy rx one online pharmacy: Pharm Express 24 – viagra target pharmacy
tramadol mexicano: best mexican online pharmacy – mexican pharmacy dr simi
mexican steroids online [url=http://pharmmex.com/#]mexican pharmacy order online[/url] online drugstore
walgreen pharmacy: buy adipex online pharmacy – ez pharmacy
top online pharmacy india: india pharmacy viagra – pharmacy in india online
http://inpharm24.com/# best online pharmacy
online medicine delivery in india: ivermectin india pharmacy – order medicines online
b pharmacy fees in india: india mart pharmacy – india e-pharmacy market size 2025
pharmacy india online [url=https://inpharm24.shop/#]InPharm24[/url] overseas pharmacy india
crestor pharmacy card: medicine online shopping – discount pharmacy card
managing warfarin therapy in various pharmacy settings: fry’s pharmacy – generic cialis india pharmacy
how much does percocet cost at pharmacy: online pharmacy weight loss – reliable online pharmacy accutane
cytotec malaysia pharmacy [url=http://pharmexpress24.com/#]online drug store[/url] target pharmacy gabapentin
best online pharmacy india: pharmacy from india – india pharmacy reviews
https://inpharm24.shop/# medical store online
unicare pharmacy artane castle opening hours: Pharm Express 24 – lipitor generic target pharmacy
french pharmacy online [url=https://pharmexpress24.com/#]Pharm Express 24[/url] riteaid pharmacy
india drug store: InPharm24 – online india pharmacy reviews
medicines online india: best pharmacy franchise in india – india pharmacy of the world
kamagra pharmacy bangkok [url=https://pharmexpress24.shop/#]Pharm Express 24[/url] buy viagra uk pharmacy
uk pharmacy no prescription: online pharmacy flonase – lamotrigine online pharmacy
pharmacy india: india pharmacy market – aster pharmacy india
https://pharmmex.com/# can you buy prescription drugs in mexico
Brand Cialis [url=https://pharmexpress24.com/#]pharmacy website[/url] metoprolol people’s pharmacy
percocet indian pharmacy: Pharm Express 24 – kaiser pharmacy hours
order medicine online: painkillers buy online – mounjaro cost mexico
online pharmacy india [url=https://inpharm24.com/#]medicine online india[/url] pharmacy in india
how to get ozempic from mexico: order mounjaro from mexico – tramadol mexico
accutane online pharmacy reviews [url=http://pharmexpress24.com/#]indian pharmacy provigil[/url] finasteride uk pharmacy
https://inpharm24.com/# online medicine delivery in india
xenical pharmacy direct: Pharm Express 24 – percocet online pharmacy without prescriptions
pharmacy name ideas in india: online medicine india – best online indian pharmacy
india pharmacy international shipping [url=https://inpharm24.shop/#]apotheke academy[/url] top online pharmacy india
viagra brand price: VGR Sources – buying sildenafil uk
discount viagra for sale: buy viagra pills online india – what does viagra do
cheap generic viagra from canada: VGR Sources – where can i get sildenafil
sildenafil 100mg canadian pharmacy [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil tabs 20mg
https://vgrsources.com/# viagra for cheap
brand viagra from canada: viagra sales – viagra canada for sale
daily viagra: VGR Sources – viagra online fast delivery
viagra online best price: VGR Sources – where to buy viagra otc
best online sildenafil prescription [url=https://vgrsources.com/#]VGR Sources[/url] cheap viagra pills online
sildenafil citrate online pharmacy: VGR Sources – price viagra 100mg
sildenafil over the counter: viagra cost comparison – best viagra tablets india
https://vgrsources.com/# generic otc viagra
generic viagra from canada: 200 mg viagra for sale – canadian online pharmacy generic viagra
buy viagra in canada [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil over the counter us
prices for viagra: us online viagra – where to order viagra online
where to buy viagra in usa: VGR Sources – sildenafil canada
viagra united states: VGR Sources – female viagra real
viagra capsules in india [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil citrate online
canadian pharmacy viagra pills: viagra 200mg uk – where to get real viagra online
https://vgrsources.com/# brand viagra 100mg price
cheap viagra 100mg canada: viagra cost in mexico – preГ§o do viagra 50mg
viagra generic discount: VGR Sources – viagra online cheap no prescription
generic viagra for sale [url=https://vgrsources.com/#]VGR Sources[/url] best rx prices for sildenafil
buy viagra australia online: VGR Sources – buy sildenafil online nz
sildenafil 100mg india: buy sildenafil no prescription – sildenafil soft tablets
sildenafil online pharmacy: buy viagra online in canada – buy viagra 100mg uk
viagra generic in mexico [url=https://vgrsources.com/#]VGR Sources[/url] us pharmacy viagra prices
authentic viagra: VGR Sources – order viagra online canada mastercard
can i buy viagra online from canada: VGR Sources – real viagra pills online
https://vgrsources.com/# brand viagra online
can you buy viagra in mexico: sildenafil over the counter india – buying viagra online
how to buy viagra in us [url=https://vgrsources.com/#]cheapest sildenafil 50 mg[/url] order viagra pills online
buying sildenafil citrate online: viagra 100mg price in india online – viagra usa online
where can you buy viagra in south africa: viagra pills australia – generic viagra mexico pharmacy
viagra online best price: buying viagra in canada – where to buy viagra online usa
sildenafil tablet brand name in india [url=https://vgrsources.com/#]viagra 100 tablet[/url] viagra for sale in australia
generic viagra uk: can you buy viagra over the counter nz – viagra pfizer price
generic viagra online pharmacy usa: VGR Sources – generic viagra discount
https://vgrsources.com/# viagra pills for men
canadian pharmacy viagra 150 mg: VGR Sources – where to buy generic sildenafil
how to order viagra in india [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil gel uk
generic viagra in us: real viagra online prescription – sildenafil pills 100mg
purchase cheap viagra: female viagra 2017 – generic sildenafil online uk
sildenafil citrate buy: VGR Sources – cipla viagra
viagra for sale in united states [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil citrate online
viagra 500: viagra online in usa – viagra coupon online
sildenafil 20 mg buy online: VGR Sources – buy viagra uk pharmacy
https://vgrsources.com/# buy viagra 100
can i buy viagra online legally: buy viagra without prescription – 100mg sildenafil 30 tablets price
generic viagra online pharmacy canada [url=https://vgrsources.com/#]VGR Sources[/url] sildenafil 25
sildenafil pills: viagra 100mg in canada – pfizer viagra online pharmacy
sildenafil for sale usa: discount viagra prices – viagra cost uk
viagra online pharmacies: viagra 25mg cost – how to get viagra in us
viagra prescription medicine: VGR Sources – 2 viagra
female viagra australia for sale [url=https://vgrsources.com/#]order sildenafil canada[/url] viagra price online
generic viagra online pharmacy usa: VGR Sources – purchase viagra 100mg
canada generic sildenafil: VGR Sources – buy viagra without rx
sildenafil online prices [url=https://vgrsources.com/#]viagra fast shipping usa[/url] viagra pharmacy coupon
https://vgrsources.com/# viagra 100 mg for sale
india viagra tablets: VGR Sources – can i buy viagra over the counter canada
buy viagra uk pharmacy: sildenafil 20 mg prescription online – online pharmacy viagra prescription
sildenafil over the counter nz: can you buy viagra canada – how do i buy viagra
viagra over the counter cost [url=https://vgrsources.com/#]VGR Sources[/url] canada pharmacy online viagra prescription
sildenafil cost compare: viagra buy online canada – viagra otc
Safe delivery in the US: Rybelsus 3mg 7mg 14mg – oral semaglutide (rybelsus)
buy prednisone online from canada: PredniPharm – PredniPharm
buying prednisone: Predni Pharm – can i buy prednisone online without a prescription
https://crestorpharm.com/# rosuvastatin calcium 10 mg price
prednisone 25mg from canada [url=https://prednipharm.shop/#]Predni Pharm[/url] Predni Pharm
lipitor cost walmart: LipiPharm – Generic Lipitor fast delivery
Semaglu Pharm: SemagluPharm – SemagluPharm
can you eat grapefruit with atorvastatin: foods to avoid with lipitor – lipitor pancreatitis
Best price for Crestor online USA [url=https://crestorpharm.shop/#]Crestor Pharm[/url] Crestor Pharm
Lipi Pharm: LipiPharm – Lipi Pharm
http://lipipharm.com/# price of lipitor
rybelsus bottle: Rybelsus side effects and dosage – Semaglu Pharm
rybelsus cost goodrx [url=https://semaglupharm.shop/#]Online pharmacy Rybelsus[/url] semaglutide dry mouth
Semaglu Pharm: Where to buy Semaglutide legally – Rybelsus 3mg 7mg 14mg
LipiPharm: Online statin drugs no doctor visit – Lipi Pharm
SemagluPharm: SemagluPharm – Semaglu Pharm
prednisone 20mg [url=http://prednipharm.com/#]Predni Pharm[/url] PredniPharm
https://crestorpharm.com/# Crestor Pharm
Crestor Pharm: CrestorPharm – Crestor mail order USA
Predni Pharm: drug prices prednisone – prednisone 60 mg price
Online pharmacy Rybelsus: what is compounded semaglutide – Semaglu Pharm
buy prednisone without a prescription: PredniPharm – prednisone acetate
rosuvastatin calcium 40 mg [url=https://crestorpharm.com/#]Buy statins online discreet shipping[/url] CrestorPharm
https://lipipharm.shop/# high intensity statin atorvastatin
Crestor Pharm: CrestorPharm – Crestor Pharm
Lipi Pharm: lipitor canada – Lipi Pharm
Predni Pharm [url=https://prednipharm.shop/#]Predni Pharm[/url] PredniPharm
SemagluPharm: Where to buy Semaglutide legally – Semaglu Pharm
can you take ashwagandha with crestor: CrestorPharm – CrestorPharm
SemagluPharm: rybelsus for sale – 14 mg rybelsus
can i buy prednisone over the counter in usa: PredniPharm – prednisone purchase canada
buy prednisone online paypal [url=http://prednipharm.com/#]Predni Pharm[/url] PredniPharm
http://crestorpharm.com/# can you take lipitor and crestor together
CrestorPharm: Rosuvastatin tablets without doctor approval – Rosuvastatin tablets without doctor approval
Semaglutide tablets without prescription: Online pharmacy Rybelsus – SemagluPharm
can you buy prednisone over the counter in mexico [url=https://prednipharm.com/#]prednisone 10 mg over the counter[/url] Predni Pharm
CrestorPharm: CrestorPharm – CrestorPharm
LipiPharm: Lipi Pharm – c2 pill atorvastatin
LipiPharm [url=http://lipipharm.com/#]Online statin drugs no doctor visit[/url] LipiPharm
Predni Pharm: prednisone 3 tablets daily – PredniPharm
https://crestorpharm.shop/# CrestorPharm
Where to buy Semaglutide legally: Semaglu Pharm – FDA-approved Rybelsus alternative
PredniPharm [url=https://prednipharm.com/#]prednisone canada pharmacy[/url] brand prednisone
CrestorPharm: Online statin therapy without RX – CrestorPharm
Predni Pharm: over the counter prednisone cheap – prednisone over the counter uk
No doctor visit required statins [url=http://crestorpharm.com/#]CrestorPharm[/url] ezetimibe vs rosuvastatin
Rybelsus online pharmacy reviews: SemagluPharm – SemagluPharm
https://prednipharm.com/# PredniPharm
https://semaglupharm.com/# Semaglu Pharm
Lipi Pharm: Affordable Lipitor alternatives USA – how fast does lipitor work
SemagluPharm [url=https://semaglupharm.com/#]semaglutide diabetes[/url] is rybelsus the same as ozempic
Predni Pharm: prednisone 1mg purchase – Predni Pharm
https://semaglupharm.shop/# Semaglu Pharm
natural semaglutide: oral semaglutide for weight loss in non diabetics – Where to buy Semaglutide legally
semaglutide diet plan pdf [url=https://semaglupharm.com/#]cheapest semaglutide[/url] Rybelsus for blood sugar control
Rybelsus online pharmacy reviews: SemagluPharm – rybelsus bottle
https://semaglupharm.shop/# semaglutide powder for compounding
http://crestorpharm.com/# Crestor Pharm
Lipi Pharm: LipiPharm – FDA-approved generic statins online
how to take atorvastatin [url=http://lipipharm.com/#]is atorvastatin a diuretic[/url] Lipi Pharm
is 80 mg of lipitor too much: п»їBuy Lipitor without prescription USA – can take lipitor with coreg
https://semaglupharm.com/# rybelsus tablets cost
CrestorPharm: cost of rosuvastatin 20 mg – Crestor Pharm
SemagluPharm [url=http://semaglupharm.com/#]SemagluPharm[/url] Safe delivery in the US
https://semaglupharm.com/# glp1 vs semaglutide
Predni Pharm: PredniPharm – prednisone best price
jardiance vs rybelsus: Semaglu Pharm – Semaglu Pharm
Semaglu Pharm [url=https://semaglupharm.shop/#]Semaglu Pharm[/url] SemagluPharm
https://semaglupharm.com/# SemagluPharm
what are the long-term side effects of rosuvastatin: crestor for high cholesterol – Crestor Pharm
Cheap Lipitor 10mg / 20mg / 40mg: Lipi Pharm – LipiPharm
https://semaglupharm.com/# como tomar rybelsus
CrestorPharm [url=https://crestorpharm.shop/#]CrestorPharm[/url] crestor rosuvastatin uses dosage side effects
LipiPharm: lipitor and grapefruit – Lipi Pharm
http://crestorpharm.com/# Affordable cholesterol-lowering pills
http://semaglupharm.com/# rybelsus without insurance
Generic Lipitor fast delivery: Lipi Pharm – Order cholesterol medication online
Semaglu Pharm [url=http://semaglupharm.com/#]Rybelsus online pharmacy reviews[/url] Semaglu Pharm
Order rosuvastatin online legally: CrestorPharm – rosuvastatin dementia
http://semaglupharm.com/# Semaglu Pharm
Predni Pharm: Predni Pharm – Predni Pharm
Atorvastatin online pharmacy [url=https://lipipharm.com/#]atorvastatin 10 mg uses in hindi[/url] Generic Lipitor fast delivery
50 mg prednisone tablet: PredniPharm – prednisone 20mg price
https://semaglupharm.com/# does semaglutide suppress appetite immediately
Predni Pharm [url=https://prednipharm.shop/#]Predni Pharm[/url] PredniPharm
Lipi Pharm: lipitor logo – LipiPharm
http://lipipharm.com/# LipiPharm
п»їBuy Rybelsus online USA: No prescription diabetes meds online – SemagluPharm
https://semaglupharm.com/# Semaglutide tablets without prescription
Safe delivery in the US [url=https://semaglupharm.shop/#]semaglutide and tirzepatide[/url] Rybelsus 3mg 7mg 14mg
CrestorPharm: Crestor mail order USA – Crestor Pharm
Lipi Pharm: is 20 mg of atorvastatin a low dose – Cheap Lipitor 10mg / 20mg / 40mg
http://semaglupharm.com/# Order Rybelsus discreetly
prednisone for sale online [url=https://prednipharm.shop/#]prednisone for sale online[/url] PredniPharm
drug interactions with rosuvastatin: Crestor Pharm – Crestor Pharm
Rybelsus for blood sugar control: No prescription diabetes meds online – Rybelsus for blood sugar control
http://lipipharm.com/# Discreet shipping for Lipitor
https://semaglupharm.com/# Semaglu Pharm
PredniPharm [url=https://prednipharm.com/#]prednisone brand name in usa[/url] Predni Pharm
Safe delivery in the US: Safe delivery in the US – No prescription diabetes meds online
https://semaglupharm.com/# Semaglu Pharm
mexican pharmaceuticals online [url=http://medsfrommexico.com/#]Meds From Mexico[/url] purple pharmacy mexico price list
India Pharm Global: India Pharm Global – India Pharm Global
https://canadapharmglobal.com/# best canadian online pharmacy reviews
reliable canadian pharmacy: Canada Pharm Global – canadian drug pharmacy
https://indiapharmglobal.com/# India Pharm Global
canadian drug [url=https://canadapharmglobal.shop/#]legitimate canadian online pharmacies[/url] my canadian pharmacy reviews
http://indiapharmglobal.com/# cheapest online pharmacy india
safe online pharmacies in canada: Canada Pharm Global – canadapharmacyonline com
buying prescription drugs in mexico: mexican mail order pharmacies – Meds From Mexico
http://canadapharmglobal.com/# northwest pharmacy canada
top 10 online pharmacy in india: Online medicine home delivery – reputable indian online pharmacy
indian pharmacy paypal [url=https://indiapharmglobal.shop/#]India Pharm Global[/url] indianpharmacy com
https://medsfrommexico.com/# medication from mexico pharmacy
India Pharm Global: india pharmacy – indian pharmacies safe
https://medsfrommexico.com/# Meds From Mexico
india online pharmacy: reputable indian online pharmacy – indian pharmacy
Meds From Mexico [url=https://medsfrommexico.com/#]mexican mail order pharmacies[/url] mexican border pharmacies shipping to usa
canadian pharmacy near me: canadian pharmacy prices – vipps approved canadian online pharmacy
https://canadapharmglobal.shop/# canadian pharmacy checker
top 10 online pharmacy in india: India Pharm Global – world pharmacy india
http://medsfrommexico.com/# Meds From Mexico
best india pharmacy [url=https://indiapharmglobal.shop/#]India Pharm Global[/url] India Pharm Global
reputable mexican pharmacies online: mexican rx online – Meds From Mexico
http://canadapharmglobal.com/# buying drugs from canada
India Pharm Global: top online pharmacy india – India Pharm Global
India Pharm Global [url=https://indiapharmglobal.shop/#]top 10 pharmacies in india[/url] indian pharmacy
Meds From Mexico: best online pharmacies in mexico – mexican mail order pharmacies
https://canadapharmglobal.shop/# canadian pharmacy 365
India Pharm Global: best india pharmacy – india pharmacy
https://indiapharmglobal.shop/# India Pharm Global
canadian pharmacy oxycodone [url=http://canadapharmglobal.com/#]Canada Pharm Global[/url] canada cloud pharmacy
mexican border pharmacies shipping to usa: buying from online mexican pharmacy – Meds From Mexico
https://medsfrommexico.shop/# Meds From Mexico
India Pharm Global: п»їlegitimate online pharmacies india – buy medicines online in india
canada discount pharmacy [url=https://canadapharmglobal.com/#]Canada Pharm Global[/url] online pharmacy canada
https://indiapharmglobal.com/# India Pharm Global
canada ed drugs: trustworthy canadian pharmacy – legitimate canadian mail order pharmacy
п»їlegitimate online pharmacies india: India Pharm Global – top 10 pharmacies in india
http://canadapharmglobal.com/# pharmacy rx world canada
http://indiapharmglobal.com/# reputable indian pharmacies
Rask Apotek: cream of tartar apotek – blodtypetest apotek
EFarmaciaIt: dove acquistare cialis online sicuro paypal – EFarmaciaIt
Papa Farma [url=http://papafarma.com/#]Papa Farma[/url] Papa Farma
http://papafarma.com/# farmacias con envÃo gratis sin pedido mÃnimo
farmacia getafe 3: Papa Farma – vibrador para hombres
Papa Farma: Papa Farma – Papa Farma
https://svenskapharma.com/# Svenska Pharma
http://svenskapharma.com/# Svenska Pharma
Svenska Pharma [url=https://svenskapharma.com/#]mammakläder rea[/url] rea mammakläder
bianacid in english: Papa Farma – Papa Farma
Papa Farma: Papa Farma – biretix gel limpiador opiniones
http://raskapotek.com/# Rask Apotek
Rask Apotek [url=https://raskapotek.com/#]beste nettapotek[/url] keratosis pilaris krem apotek
https://raskapotek.com/# proteindrikke apotek
Rask Apotek: maske ffp2 apotek – Гёyekrem apotek
https://efarmaciait.com/# cialis 100 mg prezzo
wegovy spania [url=https://papafarma.shop/#]tadalafilo 5 mg opiniones[/url] fatmacia online
Svenska Pharma: viktminskning tabletter apotek – dildo billig
apotek snorking: Rask Apotek – ortose ankel apotek
https://papafarma.com/# Papa Farma
capillarema a cosa serve [url=http://efarmaciait.com/#]EFarmaciaIt[/url] farmacia uno 1
https://raskapotek.com/# hiv hjemmetest apotek
farmacia gran canaria: ozempic agotado – ozempic tenerife
EFarmaciaIt: tadalafil prezzo 5 mg – EFarmaciaIt
https://efarmaciait.shop/# shop online 24 recensioni
EFarmaciaIt [url=https://efarmaciait.com/#]EFarmaciaIt[/url] augmentin supposte adulti
nГ¤tapoteket: Svenska Pharma – apotek vitamin d
energidrikk apotek: Rask Apotek – nГ¦ringsdrikk apotek
http://svenskapharma.com/# Svenska Pharma
melatonina 10 mg [url=https://papafarma.com/#]Papa Farma[/url] Papa Farma
https://papafarma.com/# Papa Farma
Svenska Pharma: Svenska Pharma – apotek opening hours
https://papafarma.com/# dolmen valladolid
farmacia cerca de mГ: Papa Farma – Papa Farma
EFarmaciaIt [url=https://efarmaciait.com/#]augmentin prezzo con ricetta[/url] rosuvastatina 10 mg originale
nicetile compresse a cosa serve: eritritolo prezzo – EFarmaciaIt
https://raskapotek.shop/# Rask Apotek
diabetes test apotek: Svenska Pharma – Svenska Pharma
bakteriell vagose apotek [url=http://raskapotek.com/#]nГҐl apotek[/url] oksygenmГҐler apotek
https://raskapotek.shop/# drГҐpeteller apotek
https://svenskapharma.com/# billigt te
Rask Apotek: Rask Apotek – farmasi apotek
bifidobacterium infantis apotek: ormekur hund apotek – Rask Apotek
http://raskapotek.com/# tisseunderlag apotek
fordГёyelsesenzymer apotek [url=https://raskapotek.shop/#]Rask Apotek[/url] Rask Apotek
Papa Farma: Papa Farma – boqueras embarazo
online lГ¤kare recept: Svenska Pharma – Svenska Pharma
http://efarmaciait.com/# EFarmaciaIt
progesteronkrem apotek [url=https://raskapotek.shop/#]Rask Apotek[/url] l-theanine apotek
https://papafarma.shop/# Papa Farma
https://efarmaciait.com/# EFarmaciaIt
http://medicijnpunt.com/# MedicijnPunt
PharmaJetzt [url=https://pharmajetzt.com/#]Pharma Jetzt[/url] online apotheke ohne rezept
https://pharmaconnectusa.com/# PharmaConnectUSA
Pharma Jetzt: PharmaJetzt – medikamente online gГјnstig
https://pharmaconfiance.shop/# médicament tadalafil 5 mg
internet pharmacy manitoba [url=https://pharmaconnectusa.com/#]PharmaConnectUSA[/url] PharmaConnectUSA
https://pharmaconfiance.shop/# Pharma Confiance
digitale apotheek: Medicijn Punt – MedicijnPunt
https://pharmaconnectusa.com/# lorazepam usa pharmacy
https://pharmaconfiance.shop/# le chat gel douche
versandapotheke vergleich [url=http://pharmajetzt.com/#]bad apotheke online[/url] PharmaJetzt
apotheke medikamente liefern: versandapotheken in deutschland – online-apotheke testsieger
avodart pharmacy: online pharmacy no scripts – community pharmacy
https://medicijnpunt.com/# medicijnen zonder recept
rx discount pharmacy hazard ky [url=https://pharmaconnectusa.shop/#]Pharma Connect USA[/url] PharmaConnectUSA
buy naltrexone from trusted pharmacy: Pharma Connect USA – PharmaConnectUSA
https://medicijnpunt.shop/# apotheek producten
shop apothek: apotehke – Pharma Jetzt
https://pharmaconfiance.shop/# la pharmacie le plus proche
PharmaJetzt [url=http://pharmajetzt.com/#]PharmaJetzt[/url] Pharma Jetzt
online animal pharmacy: PharmaConnectUSA – PharmaConnectUSA
clozapine registry pharmacy: best online pharmacy without prescriptions – banfield online pharmacy
http://pharmaconfiance.com/# Pharma Confiance
protГЁge-nez mГ©dical [url=http://pharmaconfiance.com/#]Pharma Confiance[/url] metronidazole ordonnance ou pas
versand apotheke auf rechnung: Pharma Jetzt – online apo
http://medicijnpunt.com/# Medicijn Punt
https://pharmajetzt.com/# apotheke per rechnung
MedicijnPunt: online pharmacy – Medicijn Punt
digitale apotheek [url=http://medicijnpunt.com/#]Medicijn Punt[/url] MedicijnPunt
friendly rx pharmacy: Pharma Connect USA – PharmaConnectUSA
http://pharmaconfiance.com/# ou se procurer du viagra
Pharma Jetzt: luitpold apotheke mediherz – online apotheke germany
PharmaConnectUSA [url=http://pharmaconnectusa.com/#]cymbalta pharmacy checker[/url] Pharma Connect USA
Pharma Connect USA: Pharma Connect USA – Pharma Connect USA
http://pharmaconfiance.com/# medecin homeopathe autour de moi
apothwke: apotheken online bestellen – PharmaJetzt
http://pharmaconnectusa.com/# buy cialis us pharmacy
online pharmacy uk doxycycline [url=http://pharmaconnectusa.com/#]reliable rx pharmacy reviews[/url] PharmaConnectUSA
https://medicijnpunt.com/# de apotheek
Pharma Connect USA: Pharma Connect USA – provigil international pharmacy
spray nasal chien: livraison medicament bordeaux – Pharma Confiance
Pharma Confiance [url=https://pharmaconfiance.com/#]Pharma Confiance[/url] Pharma Confiance
https://medicijnpunt.shop/# Medicijn Punt
apoteheke: liefer apotheke – PharmaJetzt
rx city pharmacy auburn ny: mexican online pharmacy – PharmaConnectUSA
https://pharmajetzt.shop/# PharmaJetzt
https://medicijnpunt.com/# Medicijn Punt
PharmaJetzt [url=https://pharmajetzt.shop/#]PharmaJetzt[/url] online apotheken
Pharma Confiance: Pharma Confiance – Pharma Confiance
apotheke obline: medikamente online gГјnstig – PharmaJetzt
https://pharmajetzt.com/# medikament online
online medicijnen bestellen zonder recept [url=https://medicijnpunt.shop/#]Medicijn Punt[/url] medicatie bestellen online
MedicijnPunt: MedicijnPunt – recept medicijn
Pharma Confiance: boutique lourdes en ligne – meilleur shampoing 60 millions de consommateur
https://medicijnpunt.com/# Medicijn Punt
https://pharmaconnectusa.shop/# PharmaConnectUSA
MedicijnPunt [url=https://medicijnpunt.shop/#]Medicijn Punt[/url] aptoheek
pharmacie pas chГЁre en ligne: Pharma Confiance – comment prendre tadalafil 20 mg
naproxen pharmacy: Pharma Connect USA – wellbutrin indian pharmacy
https://pharmajetzt.com/# medikamente online kaufen
online-apotheke versandkostenfrei ab 10 euro [url=http://pharmajetzt.com/#]medikamente billig[/url] apotheke medikamentencheck
PharmaConnectUSA: rx pharmacy shop – the peoples pharmacy
anastrozole online pharmacy: PharmaConnectUSA – pharmacy novo venlafaxine xr
http://pharmaconfiance.com/# Pharma Confiance
Pharma Confiance [url=http://pharmaconfiance.com/#]fucidine nez[/url] Pharma Confiance
http://pharmaconnectusa.com/# PharmaConnectUSA
crГЁme fucidine sans ordonnance: Pharma Confiance – tapis indien fait main
phzrmacie: ou acheter du viagra en toute sГ©curitГ© – ghd vente privГ©e
https://pharmaconnectusa.com/# Pharma Connect USA
Pharma Jetzt [url=https://pharmajetzt.shop/#]shopapotjeke[/url] PharmaJetzt
MedicijnPunt: MedicijnPunt – mijn medicijnen bestellen
PharmaJetzt: PharmaJetzt – apotheken versand
https://pharmaconnectusa.com/# no prior prescription required pharmacy
hГ©morroГЇdes chat [url=https://pharmaconfiance.shop/#]Pharma Confiance[/url] parapharmacue
medikamente online bestellen ohne rezept: PharmaJetzt – gГјnstige apotheken
https://medicijnpunt.com/# online apotheek gratis verzending
http://medicijnpunt.com/# Medicijn Punt
apotheke niederlande: Medicijn Punt – medicijn online
Pharma Jetzt [url=https://pharmajetzt.shop/#]pillen apotheke[/url] Pharma Jetzt
groupe ggp: pharmacie telephone – viagra 25 mg durГ©e
http://pharmaconfiance.com/# fucidine nez
Pharma Confiance: parapharmacie drakkar – Pharma Confiance
apotheke medikamente [url=http://pharmajetzt.com/#]apotehke[/url] PharmaJetzt
clindamycin people’s pharmacy: rx pharmacy richland washington – Pharma Connect USA
http://pharmajetzt.com/# PharmaJetzt
http://medicijnpunt.com/# MedicijnPunt
mГ©dicament tadalafil 5 mg: viagra homme achat – viagra sans ordonnance 24h amazon
Погода [url=https://inforigin.ru/]https://inforigin.ru/[/url] .
История дня [url=http://www.istoriamashin.ru]http://www.istoriamashin.ru[/url] .
pharmacy nl [url=https://medicijnpunt.com/#]MedicijnPunt[/url] MedicijnPunt
MedicijnPunt: beste online apotheek – MedicijnPunt
http://pharmaconfiance.com/# pharmacie centre ville caen
apotheke gГјnstig: apotheker online – online aphoteke
medikamente deutschland [url=https://pharmajetzt.com/#]Pharma Jetzt[/url] Pharma Jetzt
http://medicijnpunt.com/# online medicijnen bestellen zonder recept
Pharma Connect USA: PharmaConnectUSA – Pharma Connect USA
https://pharmajetzt.shop/# apotheke ohne versandkosten
farma: dokter online medicijnen bestellen – Medicijn Punt
Pharma Confiance: nizoral shampooing france – Pharma Confiance
https://pharmajetzt.shop/# PharmaJetzt
Pharma Connect USA [url=http://pharmaconnectusa.com/#]Pharma Connect USA[/url] french pharmacy products online
Народные приметы [url=http://www.pechory-online.ru]http://www.pechory-online.ru[/url] .
medicine online: Medicijn Punt – Medicijn Punt
MedicijnPunt: apotgeek – apotheek online nl
https://medicijnpunt.com/# apotheker medicatie
Pharma Confiance: site pharmacie en ligne fiable – prix saxenda france
viagra uk online pharmacy [url=https://pharmaconnectusa.com/#]Pharma Connect USA[/url] uf pharmacy online refill
http://pharmaconfiance.com/# pharmacie de nuit montpellier
Pharma Confiance: nizoral pharmacie – Pharma Confiance
best online pharmacy: Pharma Connect USA – best online pharmacy clomid
http://pharmajetzt.com/# Pharma Jetzt
MedicijnPunt: online medicijnen bestellen met recept – online apotheek zonder recept
MedicijnPunt [url=http://medicijnpunt.com/#]MedicijnPunt[/url] MedicijnPunt
Pharma Confiance: Pharma Confiance – chaussures extra larges pieds sensibles femme
PharmaConnectUSA: Pharma Connect USA – fluconazole target pharmacy
https://medicijnpunt.com/# MedicijnPunt
https://pharmajetzt.shop/# oneline apotheke
MedicijnPunt: belgie apotheek online – apteka nl
PharmaConnectUSA: PharmaConnectUSA – spironolactone online pharmacy
PharmaJetzt [url=https://pharmajetzt.com/#]PharmaJetzt[/url] apotheke luitpold
dragon casino [url=https://dragonslotscasinos.mobi/]dragonslotscasinos.mobi[/url] .
dragon slots casino [url=https://dragonslotscasinos.net]https://dragonslotscasinos.net[/url] .
https://pharmaconfiance.shop/# Pharma Confiance
PharmaConnectUSA: online pharmacies that use paypal – PharmaConnectUSA
apteka internetowa nl: online doktersrecept – MedicijnPunt
https://pharmajetzt.shop/# apotal versandapotheke online apotheke
Pharma Confiance [url=https://pharmaconfiance.com/#]crГЁme solaire spГ©ciale piscine[/url] univers pharmacie paris
Medicijn Punt: Medicijn Punt – MedicijnPunt
MedicijnPunt: medicijn – dutch apotheek
https://medicijnpunt.com/# Medicijn Punt
PharmaJetzt: apotheke billig – Pharma Jetzt
Medicijn Punt: MedicijnPunt – Medicijn Punt
Pharma Confiance [url=https://pharmaconfiance.com/#]parapharmacie commande en ligne[/url] livraison ghd
https://pharmajetzt.com/# PharmaJetzt
The Pokies net Australia [url=https://www.thepokiesnet101.com]https://www.thepokiesnet101.com[/url] .
PharmaJetzt: gГјnstig online apotheke – PharmaJetzt
how much is adipex at the pharmacy: PharmaConnectUSA – swiss pharmacy finpecia
https://medicijnpunt.com/# online recept
pokies 111 [url=https://pokies11.com/]https://pokies11.com/[/url] .
Pharma Confiance: pharmacie en ligne viagra avec ordonnance – Pharma Confiance
http://medicijnpunt.com/# MedicijnPunt
PharmaConnectUSA [url=https://pharmaconnectusa.shop/#]buying online pharmacy[/url] online pharmacy to buy viagra
Pharma Jetzt: apotehke – PharmaJetzt
target pharmacy amoxicillin: PharmaConnectUSA – PharmaConnectUSA
https://medicijnpunt.com/# MedicijnPunt
https://medicijnpunt.shop/# Medicijn Punt
Pharma Connect USA [url=http://pharmaconnectusa.com/#]PharmaConnectUSA[/url] pharmacy scholarships tylenol
meilleur site de parapharmacie: tadalafil mГ©dicament – Pharma Confiance
apotheke versand: PharmaJetzt – online apotheken vergleich
https://medicijnpunt.com/# online apotheek 24
your pharmacy online: PharmaConnectUSA – PharmaConnectUSA
apotheek online nl: apotheek online nl – viata online apotheek
Pharma Connect USA [url=https://pharmaconnectusa.shop/#]PharmaConnectUSA[/url] cialis online uk pharmacy
sildenafil acheter en ligne: shopping pharmacie – Pharma Confiance
https://pharmajetzt.shop/# aptheke
tesco pharmacy cialis price: PharmaConnectUSA – online pharmacy with doctor consultation
https://pharmaconfiance.shop/# pharmecie
MedicijnPunt: MedicijnPunt – online doktersrecept
pharmacie bain de bretagne [url=https://pharmaconfiance.com/#]ozempic en ligne[/url] Pharma Confiance
biotherm parapharmacie: Pharma Confiance – Pharma Confiance
https://pharmajetzt.shop/# Pharma Jetzt
global pharmacy canada: CanRx Direct – legit canadian online pharmacy
drugs from canada [url=https://canrxdirect.com/#]pharmacy wholesalers canada[/url] reliable canadian pharmacy
canadian online drugstore: canada pharmacy online – reputable canadian pharmacy
http://canrxdirect.com/# my canadian pharmacy rx
https://indimedsdirect.com/# indian pharmacy
IndiMeds Direct [url=https://indimedsdirect.com/#]pharmacy website india[/url] india pharmacy mail order
https://tijuanameds.shop/# mexico pharmacies prescription drugs
IndiMeds Direct: Online medicine home delivery – best india pharmacy
northwest canadian pharmacy: CanRx Direct – canadian pharmacy in canada
https://tijuanameds.com/# п»їbest mexican online pharmacies
http://canrxdirect.com/# canadian pharmacy review
TijuanaMeds [url=https://tijuanameds.com/#]buying from online mexican pharmacy[/url] TijuanaMeds
TijuanaMeds: buying from online mexican pharmacy – mexico drug stores pharmacies
https://tijuanameds.com/# TijuanaMeds
TijuanaMeds [url=https://tijuanameds.shop/#]п»їbest mexican online pharmacies[/url] medication from mexico pharmacy
TijuanaMeds: TijuanaMeds – TijuanaMeds
https://tijuanameds.com/# TijuanaMeds
электрокарнизы [url=elektrokarniz-nedorogo77.ru]электрокарнизы[/url] .
карниз с приводом для штор [url=www.karniz-motorizovannyj77.ru/]www.karniz-motorizovannyj77.ru/[/url] .
iflow коммутатор [url=www.citadel-trade.ru/]www.citadel-trade.ru/[/url] .
best india pharmacy [url=https://indimedsdirect.shop/#]IndiMeds Direct[/url] IndiMeds Direct
какие бывают рулонные шторы [url=http://www.elektricheskie-rulonnye-shtory77.ru]http://www.elektricheskie-rulonnye-shtory77.ru[/url] .
http://canrxdirect.com/# recommended canadian pharmacies
TijuanaMeds: TijuanaMeds – TijuanaMeds
https://tijuanameds.com/# buying from online mexican pharmacy
рулонные шторки на окна [url=rulonnye-shtory-s-elektroprivodom15.ru]рулонные шторки на окна[/url] .
canadian pharmacy [url=https://canrxdirect.shop/#]CanRx Direct[/url] thecanadianpharmacy
TijuanaMeds: purple pharmacy mexico price list – mexican drugstore online
http://indimedsdirect.com/# IndiMeds Direct
canadian pharmacy online store: CanRx Direct – canadian neighbor pharmacy
india online pharmacy [url=https://indimedsdirect.com/#]top 10 online pharmacy in india[/url] IndiMeds Direct
https://canrxdirect.shop/# buy canadian drugs
sportbets [url=https://sportbets15.ru]https://sportbets15.ru[/url] .
trusted canadian pharmacy: CanRx Direct – canadian pharmacy 24 com
enclomiphene [url=https://enclomiphenebestprice.shop/#]enclomiphene online[/url] enclomiphene testosterone
https://enclomiphenebestprice.com/# enclomiphene citrate
enclomiphene for sale: enclomiphene testosterone – enclomiphene online
Farmacia Asequible: Farmacia Asequible – Farmacia Asequible
https://farmaciaasequible.shop/# casenlax solucion oral
http://rxfreemeds.com/# putney general store pharmacy
buy ambien us pharmacy [url=https://rxfreemeds.com/#]RxFree Meds[/url] alliance rx specialty pharmacy
gran farmacia murcia: serum alba – Farmacia Asequible
https://rxfreemeds.shop/# RxFree Meds
enclomiphene [url=http://enclomiphenebestprice.com/#]enclomiphene for men[/url] enclomiphene citrate
RxFree Meds: RxFree Meds – pharmacy program online
tesco pharmacy sildenafil: xlpharmacy generic cialis – RxFree Meds
https://rxfreemeds.com/# RxFree Meds
https://farmaciaasequible.shop/# Farmacia Asequible
licoforte 40 mg [url=https://farmaciaasequible.shop/#]Farmacia Asequible[/url] Farmacia Asequible
enclomiphene citrate: enclomiphene buy – enclomiphene for sale
vimovo opiniones para el dolor lumbar: Farmacia Asequible – pharma tgm
888 starz скачать [url=http://www.https://888starz-skachat-na-android.com]888 starz скачать[/url] .
enclomiphene buy [url=https://enclomiphenebestprice.shop/#]enclomiphene for sale[/url] enclomiphene citrate
https://farmaciaasequible.shop/# Farmacia Asequible
buy enclomiphene online: enclomiphene for men – enclomiphene testosterone
enclomiphene price: enclomiphene citrate – buy enclomiphene online
https://enclomiphenebestprice.com/# enclomiphene
Farmacia Asequible [url=http://farmaciaasequible.com/#]dietГ©tica central telГ©fono[/url] Farmacia Asequible
https://enclomiphenebestprice.shop/# enclomiphene citrate
cialis 5 mg genГ©rico precio: farmacias online fiables – Farmacia Asequible
direct farmacia: Farmacia Asequible – Farmacia Asequible
https://rxfreemeds.shop/# RxFree Meds
pharmacy usa store [url=https://rxfreemeds.shop/#]RxFree Meds[/url] tesco pharmacy cialis price
farmacias 24 horas valencia: Farmacia Asequible – Farmacia Asequible
enclomiphene price: enclomiphene – enclomiphene best price
http://farmaciaasequible.com/# farmcias
Farmacia Asequible [url=https://farmaciaasequible.shop/#]tadalafil online[/url] farmacias vigo abiertas hoy
888starz скачать на андроид ру [url=http://https://888starz-starz888.ru/]888starz скачать на андроид ру[/url] .
https://farmaciaasequible.shop/# Farmacia Asequible
RxFree Meds: river pharmacy baclofen – low dose naltrexone skip’s pharmacy
http://farmaciaasequible.com/# Farmacia Asequible
enclomiphene: enclomiphene best price – enclomiphene buy
RxFree Meds [url=http://rxfreemeds.com/#]venlor xr generic effexor xr pharmacy[/url] RxFree Meds
Farmacia Asequible: Farmacia Asequible – para quГ© sirve el vimovo
http://enclomiphenebestprice.com/# enclomiphene buy
Farmacia Asequible: Farmacia Asequible – Farmacia Asequible
enclomiphene testosterone [url=https://enclomiphenebestprice.com/#]enclomiphene for sale[/url] enclomiphene citrate
прогноз на сегодня на спорт [url=www.prognoz-na-segodnya-na-sport1.ru/]прогноз на сегодня на спорт[/url] .
fioricet online pharmacy: RxFree Meds – RxFree Meds
http://farmaciaasequible.com/# Farmacia Asequible
https://farmaciaasequible.com/# Farmacia Asequible
как сыграют сегодня в футбол прогноз [url=https://www.kompyuternye-prognozy-na-futbol.ru]https://www.kompyuternye-prognozy-na-futbol.ru[/url] .
enclomiphene best price [url=https://enclomiphenebestprice.shop/#]enclomiphene for men[/url] enclomiphene price
enclomiphene buy: enclomiphene citrate – enclomiphene for sale
https://farmaciaasequible.shop/# Farmacia Asequible
RxFree Meds: wegmans pharmacy free lipitor – cialis from us pharmacy
Farmacia Asequible [url=http://farmaciaasequible.com/#]Farmacia Asequible[/url] farmacia garrido
https://farmaciaasequible.com/# wegovy medicamento
https://enclomiphenebestprice.shop/# enclomiphene price
enclomiphene: enclomiphene online – enclomiphene for sale
RxFree Meds: online pharmacy no prescription prednisone – clozapine hospital pharmacy
capsule online pharmacy [url=http://rxfreemeds.com/#]pharmacy store in india[/url] RxFree Meds
https://farmaciaasequible.com/# Farmacia Asequible
Farmacia Asequible: farmasi opiniones – Farmacia Asequible
http://enclomiphenebestprice.com/# enclomiphene testosterone
mostbet aviator oyunu [url=https://www.mostbet4042.ru]https://www.mostbet4042.ru[/url]
enclomiphene price [url=https://enclomiphenebestprice.shop/#]buy enclomiphene online[/url] enclomiphene best price
people’s pharmacy prozac: RxFree Meds – buy viagra at pharmacy
http://farmaciaasequible.com/# Farmacia Asequible
RxFree Meds: RxFree Meds – save rx pharmacy
высокие горшки кашпо напольные [url=https://www.kashpo-napolnoe-msk.ru]https://www.kashpo-napolnoe-msk.ru[/url] .
https://rxfreemeds.com/# RxFree Meds
RxFree Meds [url=https://rxfreemeds.com/#]RxFree Meds[/url] RxFree Meds
enclomiphene: enclomiphene buy – enclomiphene for sale
https://enclomiphenebestprice.shop/# enclomiphene testosterone
farmacias baratas: Farmacia Asequible – Farmacia Asequible
ana marГa lajusticia opiniones [url=http://farmaciaasequible.com/#]Farmacia Asequible[/url] tadalafilo 10
напольные цветочные горшки купить [url=http://www.kashpo-napolnoe-spb.ru]напольные цветочные горшки купить[/url] .
viagra in chennai pharmacy: RxFree Meds – finpecia online pharmacy
mostbet casino oyunları [url=http://mostbet3041.ru]http://mostbet3041.ru[/url]
https://rxfreemeds.com/# RxFree Meds
https://farmaciaasequible.com/# Farmacia Asequible
enclomiphene buy: enclomiphene for sale – enclomiphene testosterone
прогнозы на чемпионат мира по хоккею [url=https://www.luchshie-prognozy-na-khokkej.ru]https://www.luchshie-prognozy-na-khokkej.ru[/url] .
farmasi opiniones [url=http://farmaciaasequible.com/#]opiniones lГnea directa ocu[/url] remedios 24 opiniones
Farmacia Asequible: Farmacia Asequible – eucerin cacao
RxFree Meds: Sinemet – Abilify
pharmacy rx [url=https://rxfreemeds.shop/#]RxFree Meds[/url] kroger pharmacy gabapentin
888starz контора ру [url=https://888starz.com.ru/]888starz контора ру[/url] .
mostbet casino oyunları [url=http://mostbet4045.ru]mostbet casino oyunları[/url]
http://rxfreemeds.com/# singulair pharmacy prices
rx pharmacy logo: propecia price pharmacy – kaiser permanente pharmacy
http://enclomiphenebestprice.com/# enclomiphene for men
Farmacia Asequible [url=http://farmaciaasequible.com/#]farmacia a domicilio tenerife[/url] servicio tecnico braun sevilla
enclomiphene: enclomiphene price – enclomiphene best price
http://rxfreemeds.com/# RxFree Meds
viagra buy: comprar todacitan online – que es drogueria en espaГ±a
1win скачать kg [url=http://1win1138.ru/]http://1win1138.ru/[/url]
buy enclomiphene online [url=https://enclomiphenebestprice.com/#]enclomiphene testosterone[/url] enclomiphene citrate
generic viagra online: RxFree Meds – RxFree Meds
http://enclomiphenebestprice.com/# buy enclomiphene online
https://enclomiphenebestprice.shop/# enclomiphene for sale
https://enclomiphenebestprice.com/# enclomiphene price
Tinidazole [url=http://rxfreemeds.com/#]where to buy viagra pharmacy[/url] express pharmacy online
Farmacia Asequible: farmacias online baratas – opiniones iraltone aga plus
super pharmacy: actos pharmacy – target pharmacy lipitor price
Farmacia Asequible [url=http://farmaciaasequible.com/#]taxfree alicante[/url] Farmacia Asequible
xeloda online pharmacy: RxFree Meds – target pharmacy lipitor generic
Farmacia Asequible: farmacia cerca de mi abierta hoy – Farmacia Asequible
перепланировка комнаты [url=https://soglasowanie-pereplanirovki-kvartiry.ru/]перепланировка комнаты[/url] .